-

How to clear Twitter (X) cache on iPhone, Android, and desktop
If Twitter (X) is running slow, showing outdated posts, or eating up storage, clearing the cache can usually fix it. Luckily, this process is simple for both the app and the website. In this guide, we...
-
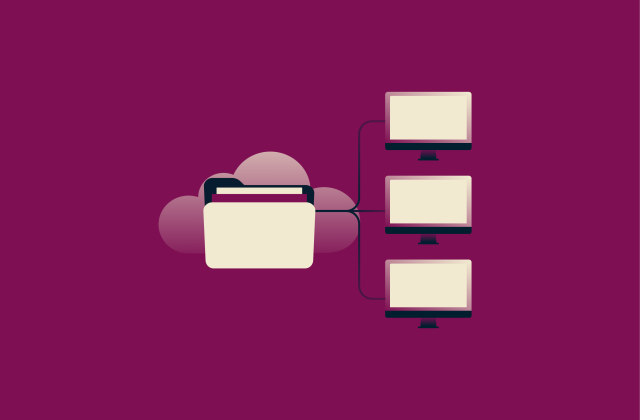
Network File System (NFS): A secure guide for remote access
The Network File System (NFS) provides multiple computers with an easy way to access the same remote folders through their regular filesystems. This article explains how NFS does that, the different v...
-

Is your Facebook account cloned? How to detect it and protect yourself
If you’ve suddenly started receiving messages from friends asking whether you created a “new” profile, your Facebook account might have been cloned. Account cloning, when someone copies your pho...
-

How to permanently delete your Apple ID: Full guide
Deleting your Apple ID is generally straightforward, but there are a few steps you should take beforehand to ensure you don’t lose access to important data or services. This guide walks you through ...
-
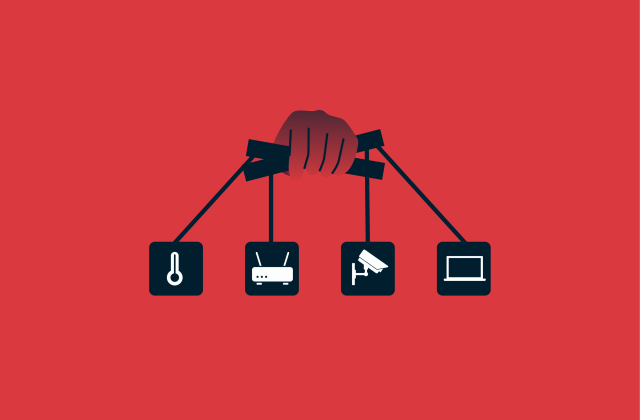
IoT botnets explained: How to detect and defeat them
Botnets were once built almost entirely from infected desktop and laptop computers. The rise of the Internet of Things (IoT) has changed that. IoT botnets exploit vulnerable connected devices at scale...
-

Military romance scams: How to protect yourself
If someone you’ve met online claims to be in the military and is asking for money, gift cards, or sensitive information or photos, pause before sending anything. These are common red flags of a mili...
-

Who owns an IP address and how a VPN keeps yours private
Think your Internet Protocol (IP) address belongs to you? Not exactly. Every time you go online, your home network and devices are identified by IP addresses that can reveal your approximate location,...
-

What is first-party data: How it’s collected and used
First-party data is information a company collects directly from people who use its website, app, or services. This includes data collected with consent, like optional cookies, as well as information ...
-

Is Honey legit? A comprehensive review of PayPal Honey
Honey is a legitimate browser extension and mobile app owned by PayPal. It automatically searches for coupons, tracks prices, and offers rewards when you shop online. Like many shopping tools, it coll...
-

Is your Ring doorbell hacked? Here’s how to tell and protect it
If your Ring doorbell is turning on when it shouldn’t or otherwise behaving strangely, you might worry that it’s been hacked. A compromised Ring device can result in a serious invasion of your pri...
Featured





