What is typosquatting? How it works and how to stay safe

Mistyping a URL seems harmless, but it can quietly expose you to one of the oldest tricks used by cybercriminals: typosquatting. In this article, we break down what typosquatting is, how it works, and how to spot it. We also cover the risks it poses and the tools that can help protect you.
Note: Typosquatting is unethical, illegal in many jurisdictions, and can put people at risk. This article is provided for educational and defensive purposes only.
What is typosquatting?
Typosquatting is the practice of registering domain names that look nearly identical to a popular website’s domain name, usually with a small typo or character swap, with the intent of capturing traffic from users who make typing errors. As an example, a cybercriminal may purchase the domain googel.com with the intent of capturing users looking for google.com.
Once they have a potential victim on the fake site, they have multiple attack vectors available, including phishing, malware, or adware.
Is typosquatting illegal?
Yes, when done in bad faith, typosquatting is illegal and often violates trademark laws. In the U.S. it violates the Anticybersquatting Consumer Protection Act (ACPA). This law allows trademark owners to sue if someone registers a domain confusingly similar to their brand in bad faith.
There have been several high-profile cases where brands took the typosquatters to court and won large settlements. The courts can order the domain to be transferred or canceled and may award statutory damages to the trademark owner.
That said, not every typo-based domain is automatically illegal. Some may be used for parody, education, or non-commercial purposes. A popular example is guthib.com, a misspelling of GitHub that displays a large “You spelled it wrong” banner. The legality depends on intent, usage, and whether it infringes on a protected trademark.
Typosquatting vs. cybersquatting: Key differences
The objective of a cybersquatting attack is different from typosquatting. Instead of going after unsuspecting targets, cybersquatters register domain names that resemble legitimate brands or websites, not to use them for scams, but with the intent to profit, usually by selling it back to the rightful owner.
Cybersquatters typically target domains of a new company or brand that doesn’t have a website yet, while some use a similar tactic to typosquatting by buying a similar URL. Like typosquatting, cybersquatting also violates trademark laws.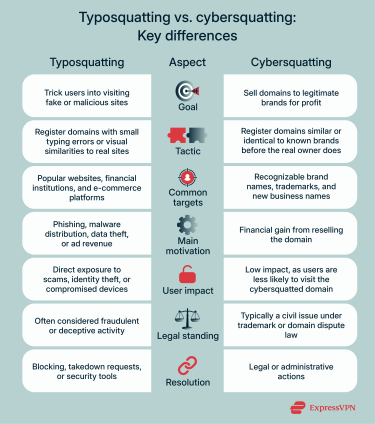
Key statistics and trends
Typosquatting continues to rise worldwide, with growing numbers of fake domains, phishing incidents, and legal disputes reported each year. Recent data from cybersecurity and trademark authorities shows how widespread and persistent this threat has become.
- Average lookalike domains per brand: The Fortra 2023 Domain Impersonation Report found that in the first half of 2023, the average brand was targeted by nearly 40 lookalike URLs each month. That number jumped to an average of 73 in Q2 of 2024.
- Active malicious lookalike domains: Zscaler ThreatLabz analyzed typosquatting and brand impersonation from February 2024 to July 2024 and found that out of 30,000 lookalike domains, over 10,000 were malicious.
- Top targeted brands for impersonation: For the same period, ThreatLabz found that Google, Microsoft, and Amazon collectively accounted for nearly 75% of impersonation-based domains.
- Use of HTTPS certificates on lookalike domains: ThreatLabz also revealed that nearly half of the malicious lookalike domains studied in 2024 used free Secure Sockets Layer (SSL) certificates provided by Let’s Encrypt to appear credible.
- Most targeted industries for typosquatting attacks: The internet services, professional services, and online shopping sectors accounted for over 77% of typosquatting-related phishing domains in ThreatLabz analysis. This was likely driven by these industries’ large user bases, dealings with sensitive data, and frequent payment activity.
How typosquatting works
Typosquatting relies on how browsers and the Domain Name System (DNS) handle domain names. When someone enters a URL, the browser will bring you to the website that exactly matches what you typed: it doesn’t try to correct small mistakes or guess what was intended. Attackers take advantage of this by registering domains that differ from the real one in a minor way.
URL phishing attacks, where attackers send emails or text, also present a major problem. As the user, you only see the text with the link, with the link destination itself not immediately visible. If you click it without taking the time to verify that the link goes to the legitimate domain, you may end up on a typosquatted site.
Once a typosquatted domain is registered, the attacker can use the fake domain for several malicious purposes. Many typosquatters create and manage large numbers of lookalike domains at once.
Common tactics used by typosquatters
Cybercriminals can impersonate domains and trick users in a variety of ways:
- Typographical errors: Typosquatters often rely on small, visually subtle changes to well-known domains. This can include inserting, removing, or altering characters in ways that resemble everyday typing mistakes.
- Different top-level domain (TLD): Attackers may register domains that use a different TLD to the legitimate website while keeping the rest of the address the same or similar. For example, google.info instead of google.com.
- Hyphenated or misspelled brand names: Some typosquatted domains alter the original name by inserting punctuation or using minor spelling changes that are very difficult to spot at a glance. This method is especially used in emails or search results where users focus on the brand name rather than the full address.
- Combo-squatting: By combining a brand name with a common or authoritative-sounding word, such as terms related to support, security, or account access, attackers can give their fake site an air of legitimacy. These domains feel authoritative because the added word reinforces the impression of a legitimate purpose.
- Fake subdomains: This tactic relies on how URLs are displayed and read. With a fake subdomain, a familiar brand name appears at the start of a much longer address, even though the actual domain belongs to someone else. Because many apps and mobile devices shorten long URLs, only the first portion may be visible, making the link seem legitimate.
- Homograph attacks: Cybercriminals can use characters from different writing systems that look nearly identical to standard letters. These visually similar characters allow a fake domain to appear identical to the legitimate one, even though the relevant link leads somewhere entirely different. The differences aren’t obvious to users because the variation exists in the underlying encoding rather than in the visible text.
Types of typosquatting attacks
Once a user lands on a typosquatted domain, attackers can misuse this access in many different ways. Here are some of the most common tactics: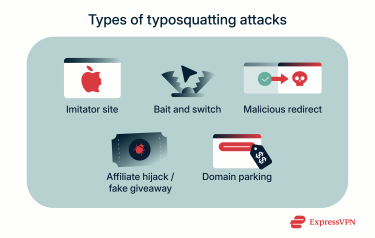
- Imitator sites: When someone lands on an impostor site, they’re met with nearly identical design, colors, logo, and elements as the legitimate site. The goal is simple: trick users into handing over data that they believe they’re giving to the real site.
- Bait-and-switch scams: In this version of typosquatting, the attacker uses a similar domain to pull someone in but then shows something completely different to the legitimate site once they arrive. The site might push fake offers, questionable products, or other misleading content. Attackers may then use the methods described below to profit off the user.
- Malicious redirects and drive-by downloads: Some typosquatting domains redirect users to malicious pages or trigger hidden scripts that install malware.
- Affiliate hijacking: Affiliate hijacking is when bad actors spoof a brand’s paid search ads or create typosquatted versions to intercept legitimate traffic and claim affiliate commissions. They use nearly identical headlines and URLs to mislead users into clicking their links.
- Fake giveaways: Attackers may create enticing brand promotions in an effort to trick users into handing over personal data or payment information.
- Domain parking for ad revenue: Some attackers use parked domains (a domain without a website or email tied to it) to serve generic ads. Each visit earns small amounts of money through impressions or clicks. These domains can also be used to gather data on user behavior and may later pivot into more harmful activity.
Real-world examples of typosquatting
Security researchers and media reports have documented numerous typosquatting incidents affecting major companies, digital platforms, and online services. Here are some examples:
- Lookalike financial and retail domains: Investigations have found typo-based domains designed to resemble large banking or retail websites, exposing users to credential theft or malicious redirects.
- Affiliate-driven traffic diversion: Some cases have involved groups registering common typo variations of brands’ domains to reroute visitors through affiliate links. Users who mistype a website name are sent to intermediary pages that ultimately lead to the legitimate site, generating unauthorized commissions for the cybercriminals.
- Imitation of well-known social platforms: Reports have described typosquatted domains crafted to resemble major social networks that may host ads, deceptive content, or phishing forms intended to capitalize on misdirected user traffic.
- Cryptocurrency lookalike sites: Researchers have observed typosquatted domains targeting users of digital asset platforms which lead to phishing pages designed to collect account credentials or wallet information.
- Malicious open-source package names: Several analyses have documented typosquatted package names uploaded to open-source registries. Developers who mistype a library name may inadvertently install harmful code, including credential-stealers or backdoor scripts. This issue has been amplified in recent years with the use of large language models (LLMs) that can occasionally suggest package names that don’t exist, which attackers can then register and weaponize.
The dangers of typosquatting
Typosquatting can expose users to a wide range of online scams and security threats, harming both individuals and businesses alike.
Financial loss and phishing risks
Users who land on fake versions of real websites may enter their credentials, credit card numbers, or personal information. Attackers can then use those details for identity theft or to make fraudulent transactions. They may also sell the data on criminal marketplaces. Even one successful attack can lead to thousands of dollars in losses for individuals and companies.
Reputational harm for brands
When a typosquatted site imitates a well-known brand, users can assume any problems they experience are the brand’s fault. If an order never shows up or the quality is far below expectations, that frustration can spill over into bad reviews, complaints, and a loss of trust. For the brand, repairing that damage isn’t simple. Rebuilding that trust takes time and often requires expensive PR campaigns.
How to protect yourself from typosquatting
The easiest way to avoid typosquatting is to search for the website rather than typing the URL manually. Search engines are generally reliable at displaying verified, legitimate sites and can help you avoid falling victim to the small typing errors that cybercriminals rely on. Beyond that, here are some more of the best practices that can help you stay protected: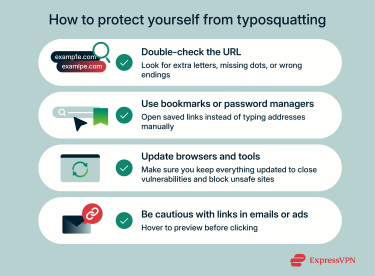
Double-check website addresses
If you type the URL in your browser, always take a minute to check that it matches the one you intend to visit. Look for common mistakes such as extra letters, missing characters, or incorrect hyphenation.
Use bookmarks and password managers
Instead of relying on your typing skills every time you go to your online bank or favorite gaming site, add it as a browser bookmark. Then you can have quick access to the site without having to go to the search engine or worry about typos.
Another option is relying on a secure password manager like ExpressVPN Keys. It won’t help you avoid typosquatting sites, but it won’t autofill your credentials if the domain isn’t correct or verified.
Keep browsers and security tools updated
Your browser can be a reliable defense against some typosquatting sites. Many of them come with built-in security tools like Google Safe Browsing or Microsoft Defender SmartScreen that detect and block potentially malicious or harmful websites. Make sure you update your browser to the latest version so you’ll have up-to-date protection against newly registered malicious sites.
You should also have security tools like antivirus and anti-malware scanners for websites that get past the browser detection. They’ll stop unwanted downloads from starting and infecting your device.
Be careful with links in emails and ads
To avoid URL phishing attacks that employ typosquatting, it’s recommended to hover your mouse over links and ads to view the full URL before you click it. Be sure to check the domain thoroughly for typos, and also confirm that the TLD is consistent with the legitimate website.
How to protect your business against typosquatting
As a business owner, there are proactive steps you can take to reduce the risk of attackers using your brand for typosquatting scams.
Register typo variants of your domain
Purchase the most obvious typo versions of your domain and redirect them to your official website. This includes alternate spellings, versions with and without hyphens, and different TLDs, like .net, .org, or country-specific extensions. Owning these domains makes it harder for bad actors to imitate your brand, and setting up simple redirects ensures visitors always reach your legitimate site.
Use SSL and domain monitoring tools
SSL certificates help confirm that your website is legitimate and secure. They protect users’ data during transmission and give customers confidence they’re interacting with your real site. However, getting an SSL certificate isn’t difficult or expensive, so cybercriminals may be able to get SSL certificates for typosquatted domains. Due to this, in addition to having a reputable SSL certificate on your site, you should use a domain and SSL monitoring tool.
While every tool is different, find one that can do the following:
- Scan for domain variants to detect typosquatting and homoglyph attacks.
- Track SSL certificates issued with your brand name or keywords.
- Identify clone sites through design and content analysis.
- Send real-time alerts to your team for fast response.
- Assist with takedowns by providing templates and registrar contacts.
Educate employees and stakeholders
Your employees and customers are your first line of defense. Train them to recognize suspicious URLs, unexpected login pages, and red flags in emails that can signal a phishing or typosquatting attack. Encourage staff to always access key services using bookmarks or search engines rather than typing addresses manually.
Report or take down malicious domains
If you’ve already been targeted, it’s not too late to act. The Internet Corporation for Assigned Names and Numbers (ICANN) Uniform Domain Name Dispute Resolution Policy (UDRP) allows trademark owners to challenge and recover fraudulent domains registered in bad faith.
You can file a complaint through an accredited provider such as the World Intellectual Property Organization (WIPO) to initiate a takedown or transfer process. In severe cases, you may wish to consult a legal expert and explore options under the Anticybersquatting Consumer Protection Act (ACPA) or equivalent local laws.
How VPNs help prevent typosquatting attacks
A virtual private network (VPN) can prevent you from accessing some typosquatted domains if it has DNS filtering that blocks known malicious or suspicious domains. If you do end up on a typosquatted site, a VPN can still limit what data the site is able to gain from you by hiding your real IP address and location.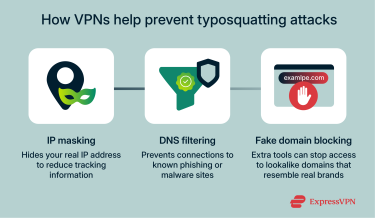
IP address masking and reduced tracking
When you connect to a VPN, it hides your real IP address from the sites you visit. This makes it harder for malicious sites to ascertain your location or tie your visit to other activity. With less information to work with, attackers may struggle to follow up with targeted scams, location-based attacks, or further tracking attempts.
DNS filtering and malware protection
Some VPNs use their own DNS servers that include security filtering or malicious site blockers, like ExpressVPN’s Threat Manager. With these features on, every website address you try to visit is checked against a list of known malicious or suspicious domains. If you mistakenly try to access a typosquatted site that’s on this list, the connection will be stopped.
VPN and antivirus: A stronger defense together
A VPN on its own can limit what a malicious site learns about you, but it can’t stop every threat that might follow a visit to such a site. That’s where antivirus tools come in: they can catch unsafe downloads, block harmful scripts, and flag suspicious activity on your device.
Used together, the two tools cover different parts of the problem. The VPN helps protect your privacy, while the antivirus focuses on stopping any malware that may try to infect your device.
FAQ: Questions about typosquatting
What happens if I visit a typosquatted site?
Such sites can expose you to phishing scams, malware downloads, or fake login pages. Some may also host intrusive ads or redirect you to unsafe pages.
How can I recover from a typosquatting attack?
If you entered personal information on a fake website, change your passwords right away and, if possible, enable multi-factor authentication (MFA). Then, run a full antivirus scan and monitor your financial accounts for suspicious activity. If the attack involves your business, you can report the domain.
Are there tools to detect typosquatted domains?
You can use a domain monitoring tool that can alert you when new domains resembling your brand are registered. Some also use Secure Sockets Layer (SSL) certificate tracking and content analysis to find copycat websites.
Can a VPN protect against typosquatting?
A VPN with Domain Name System (DNS) filtering can prevent access to some typosquatted sites. However, it likely will not be able to prevent access to every one of these sites. However, even if you do end up on a typosquatted domain, a VPN can hide your IP address, limiting the amount of data attackers can collect.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN