Malgent removal guide (Trojan:Win32/Malgent)

If you've received a security alert for Trojan:Win32/Malgent, it's important to take steps to resolve it. Microsoft’s security intelligence identifies Win32/Malgent as a trojan, which is a type of malware that masquerades as a legitimate program. Trojans can have devastating effects, ranging from deleting your files to providing attackers with full access to your system.
This guide provides clear Malgent removal instructions to help you secure your computer and protect your private data. It also includes details on how to recognize a Malgent infection and how to protect your device against future threats.
What is Malgent (Trojan:Win32/Malgent)?
Malgent, short for Malicious Agent, is a name used to identify a specific family of trojan malware that can act as a gateway for further malware once it infects your system.
Note: MacOS is not vulnerable to this particular trojan family.
General characteristics of trojan malware
A trojan is a type of malware that’s usually disguised as a useful application, document, or software update. Unlike some other kinds of malware like viruses, trojans can’t replicate themselves, and the users must download and execute them.
Once active, the goal of a trojan is to deliver a malicious payload. What happens next depends on the exact payload, but keystroke monitoring, screenshots of your activity, and further opening up of your system to attackers via backdoors are all possible.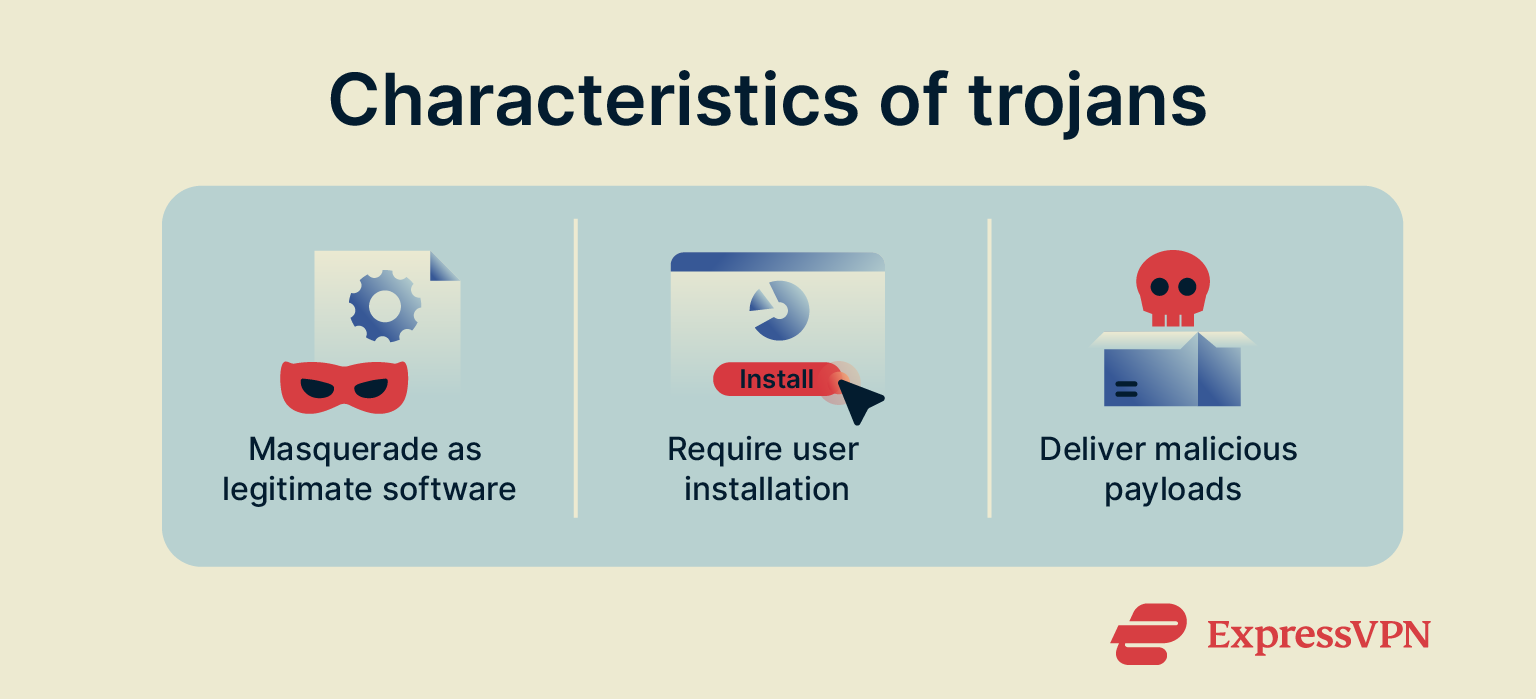
Why Malgent is dangerous
The danger of Malgent malware lies in its ability to open the door for a wide range of other cyber threats.
How Malgent spreads and operates
Much like other trojans, Malgent relies on deception to infect systems. It may arrive via phishing emails, infected ads, or malicious software downloaded from untrustworthy websites.
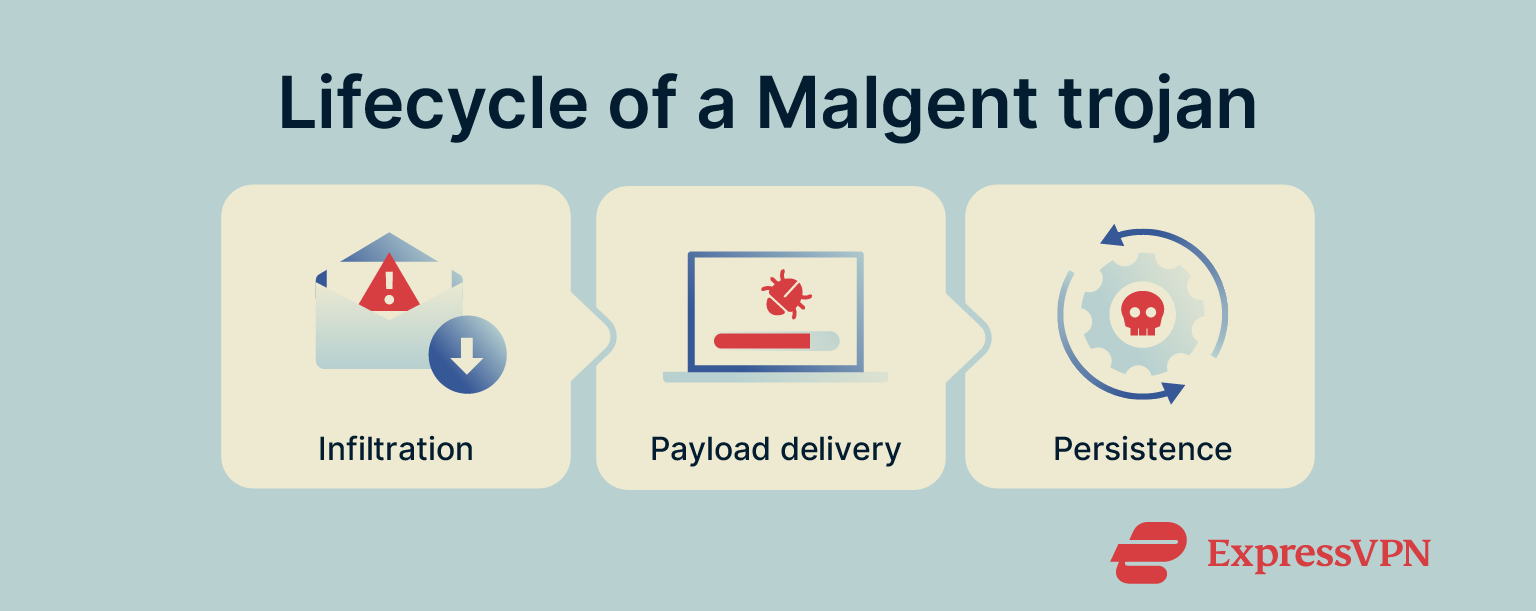
Trojans in the Malgent family typically follow three stages:
- Infiltration: The trojan enters the system through deceptive methods, like those described above.
- Payload delivery: After installation, Malgent trojans usually connect to a remote server to download and install malicious payloads, which may include spyware, adware, or ransomware.
- Persistence: To remain on the system, Malgent trojans may modify your system’s registry keys, meaning that it’s likely to evade detection and run successfully every time Windows starts. This makes it harder to detect and remove.
Risks for your system and data
A Malgent infection may compromise your device’s performance and the safety of your personal data if left unaddressed.
Data theft and privacy issues
Since trojans like Malgent can download and install spyware, they increase the risk of credential and data theft. These secondary infections can potentially capture everything you type or take screenshots of sensitive information, including bank account logins, credit card numbers, and private messages.
This stolen information can be misused for activities like identity theft and financial fraud. The attackers may also sell your personal information on the dark web.
System instability and performance problems
A slow and unstable system is one of the telltale signs of a malware infection. Trojans like Malgent and the additional malware they install can run hidden processes that heavily consume system resources.
For example, Malgent may install a crypto miner, which then uses your PC’s resources to solve complex mathematical puzzles, generating cryptocurrency for the attackers. Such malware can lead to slow system performance, frequent application crashes, and unexpected error messages.
How to recognize a Malgent infection
There are two main ways to recognize a Malgent infection. The first is a security notification from your antivirus software. The second is by spotting unusual behavior and performance issues on your PC.
Microsoft Defender alerts explained
Unless you’re using a third-party antivirus, the first sign of a Malgent infection may be a Microsoft Defender threat alert. This built-in Windows antivirus actively monitors for malicious files and alerts you if malware, including Malgent, is detected on your system. However, note that Defender might not pick up on every threat, so a lack of alerts isn’t an absolute guarantee that your system doesn’t have a Malgent infection.
How to read threat notifications
Microsoft Defender provides specific details upon finding a threat, letting you know exactly what it is. A typical notification that says Trojan:Win32/Malgent or Trojan:Win32/Malgent!MSR indicates the following key details, per Microsoft's malware naming conventions:
- Trojan: The category of malware.
- Win32: The platform it targets, which in this case is the 32-bit Windows operating system.
- Malgent: The specific name Microsoft assigns to this malware family.
- !MSR: All suffixes beginning with ‘!’ are indicators that Microsoft uses internally. In the instance of Trojan:Win32/Malgent!MSR, it identifies the specific Malware strain used by Diamond Sleet, a recognized cyber espionage group.
Microsoft Defender’s alerts will also show you one of various severity levels, ranging from Low to Severe. If a threat is rated as High or Severe, it’s highly recommended that you deal with it as quickly as possible.
What to do when Malgent is detected
If you get an alert that Malgent has been detected on your system, the first step is to investigate whether it’s a real threat or a false positive.
Some legitimate applications can be incorrectly flagged as containing Malgent trojans. These false positives can happen if a program's behavior or code resembles that of Malgent malware.
If the alert flags a file or program you recognize, trust, and downloaded from a reputable source, it may be safe. That said, always verify the affected file/program through additional tools, such as VirusTotal, to get a second opinion.
If the flagged file has an unfamiliar name or is located in a suspicious directory, it's more likely to be an actual infection, in which case you’ll need to take steps to remove it immediately.
Symptoms of Malgent on your PC
If a Malgent alert isn’t picked up (for example, if real‑time protection is disabled or it’s a new variant), you might be able to spot it by noticing performance-related symptoms, like the ones below. However, note that trojans are designed to run quietly, so there might not always be any noticeable symptoms. That’s why it’s best to have antivirus software running and to keep its definitions up-to-date.
Performance slowdowns and crashes
You may start to notice sudden and unexplained drops in your system’s performance. Programs can take longer to load, your mouse cursor may freeze, or your whole system could crash unexpectedly.
It’s possible that you have an unusually high load on your CPU and memory due to Malgent and other malware hogging all your system resources. To check this, access the Task Manager by pressing Ctrl+Shift+Esc and check your CPU and Memory usage, which is represented by a percentage. If this is abnormally high even when you’re not running any intensive programs, you may have a problem.
Unknown processes and unfamiliar files
Beyond high CPU/Memory usage, seeing unknown processes in Task Manager could indicate an infection. Keep in mind, however, that Malgent trojans often disguise themselves as legitimate programs.
To investigate, look through all the active applications in the Processes tab of Task Manager and try to find any suspicious or unrecognized entries. You might also find suspicious startup programs listed in the Startup apps tab, which could be programs the malware has set to run automatically.
Take a look at the Services tab too, and see if there are any suspicious entries set to automatic start there. Some malware will install itself as a service, which makes it more difficult to spot in the process list.
If you’re suspicious of anything in your processes or startup apps, it can help to right-click and open the containing folder. If you see something like explorer.exe, but it's not located where it should be (System32), that is a red flag.
Irregular web browser behavior
You might witness inconsistent behavior from your web browser, such as redirects to unfamiliar websites, pop-ups you’ve never seen before, or even a change in your browser’s configuration settings that you didn’t make.
Unusual network activity
Trojans can communicate with remote servers after infecting a system, so unusual network activity can be an early warning sign. Built-in Windows tools like the Resource Monitor, which you can access by typing “resmon” in the Run dialog (accessible by pressing the Windows Key + R at the same time) and pressing Enter, can help you see which processes are sending and receiving data online.
Unauthorized access warnings
Since Malgent can lead to credential and data theft, you might receive warnings about suspicious activity. These could be notifications from your bank, email, and/or social media accounts about login attempts from strange locations, indicating that your passwords may have been compromised. You might also receive alerts from your bank or credit card provider about suspicious financial transactions.
Step-by-step Malgent removal
There are a couple of ways you can remove Malgent from your system, though automatic removal is the recommended method. Here’s how to do it.
Automatic removal with Microsoft Defender and Windows Security (recommended)
Microsoft Defender may detect a Malgent infection and flag it automatically. From there, you’ll have the option to remove or quarantine the malicious files in the notification that pops up. You can quarantine the files if you wish to confirm that it isn’t a false positive, but otherwise, it’s recommended to remove them as soon as possible.
However, if Microsoft Defender hasn’t flagged Malgent automatically, but you still see symptoms and suspect an infection, the recommended approach is to perform a full scan using Windows Security. Alongside potentially detecting and removing Malgent, the full scan may also detect and remove any further malicious payloads that were downloaded onto your system.
Run a full scan in Windows Security
Windows Security is an integrated security solution that features security tools such as Microsoft Defender and Windows Firewall. With its full scan, you can check all files and system areas, unlike a quick scan that only checks areas where malware commonly hides.
If possible, disconnect from the internet before scanning to prevent any potentially malicious files from communicating with remote servers or downloading additional components.
Then, follow these steps:
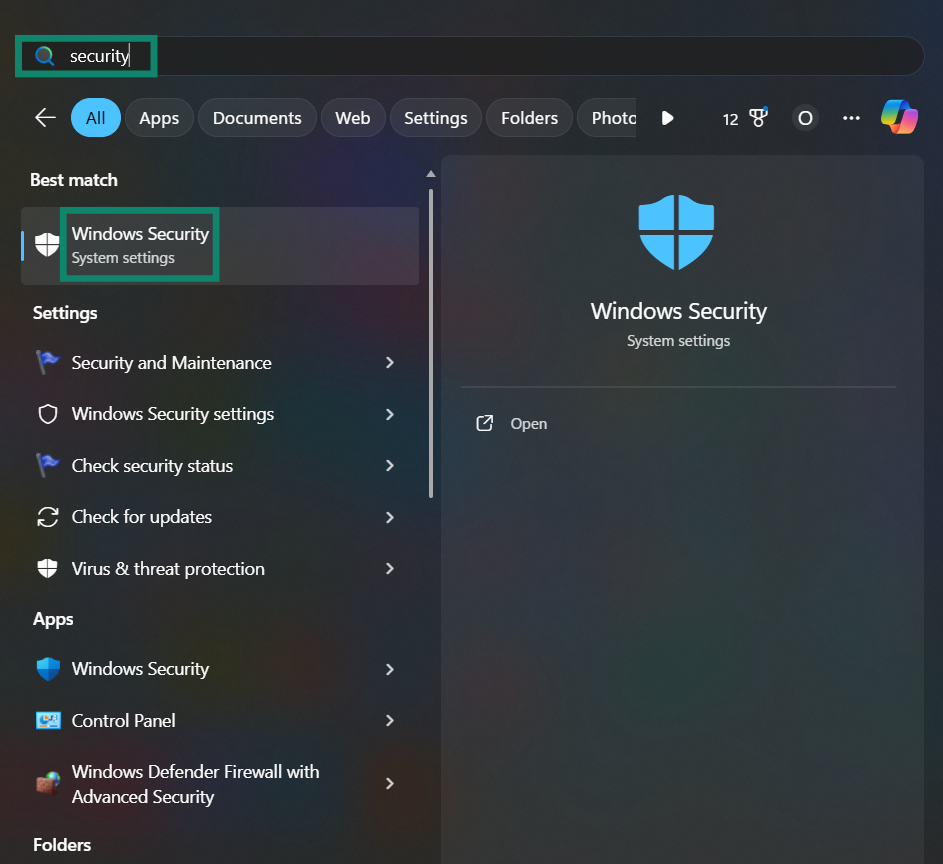
- Open the Start menu, search for Security, and click the Windows Security option. Alternatively, you can use the search function on your Windows Taskbar (bottom of the screen) instead of opening the Start menu.
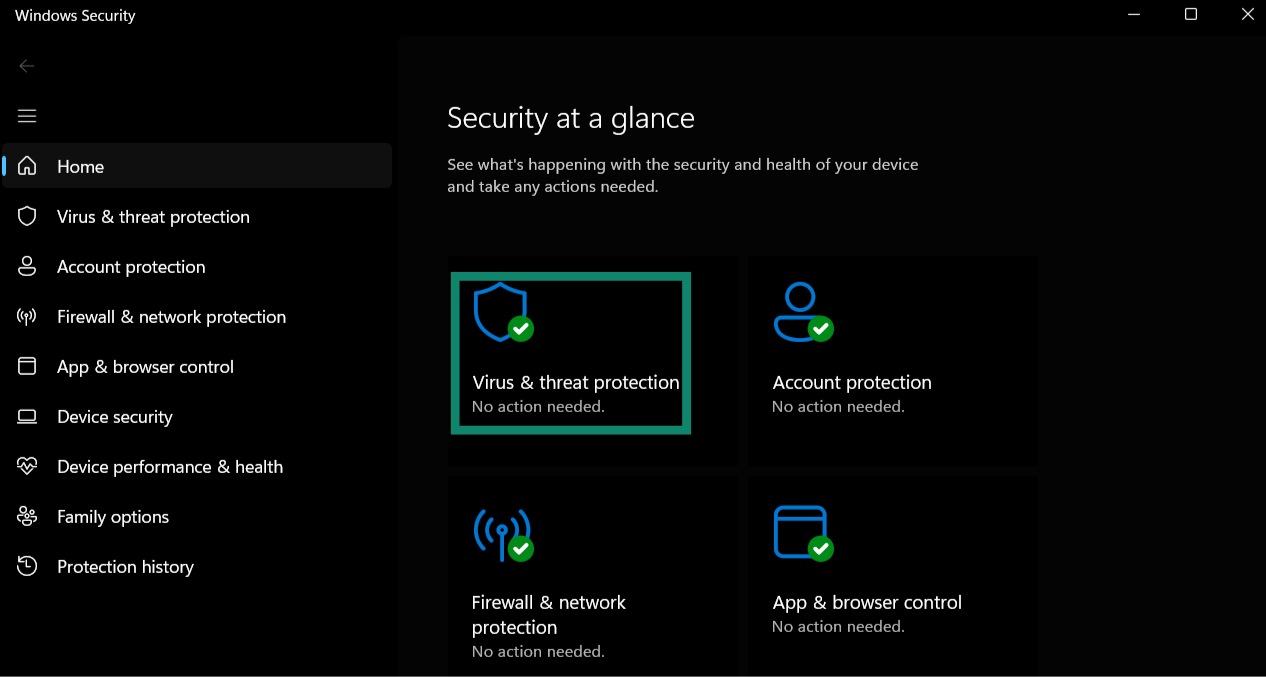
- Click on Virus & threat protection.
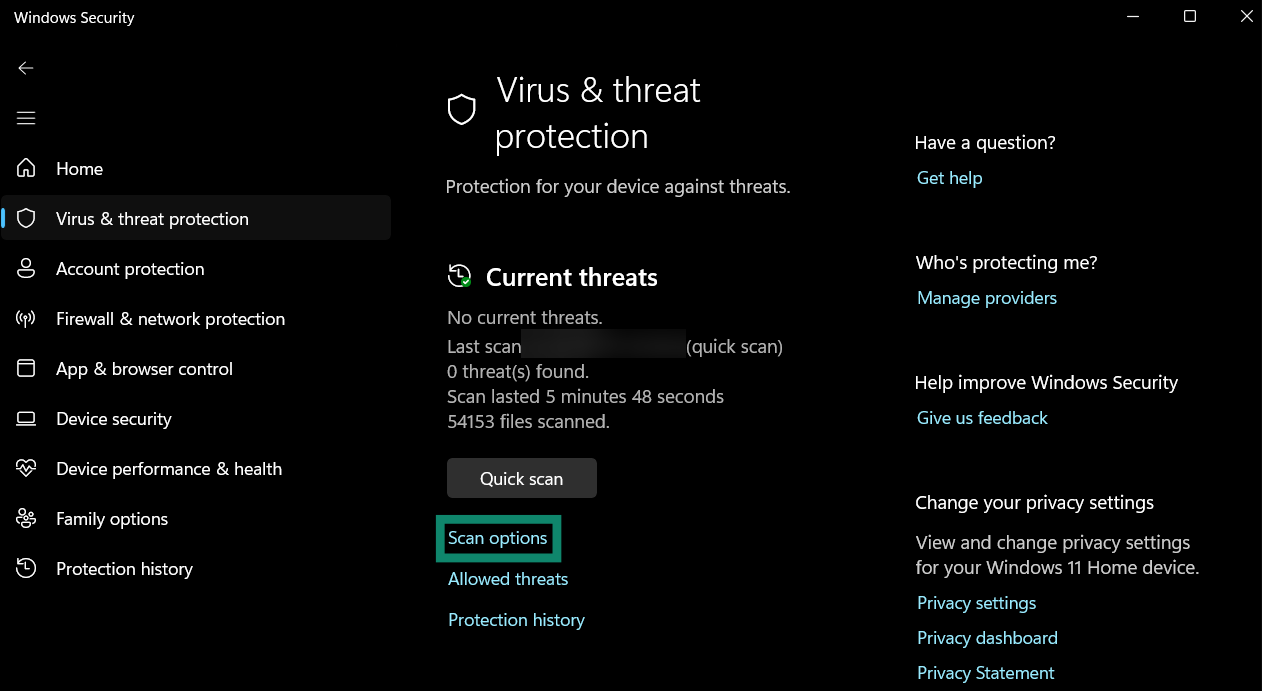
- Click the Scan options menu to see a list of available scans.
- Check the Full scan option and click Scan now.
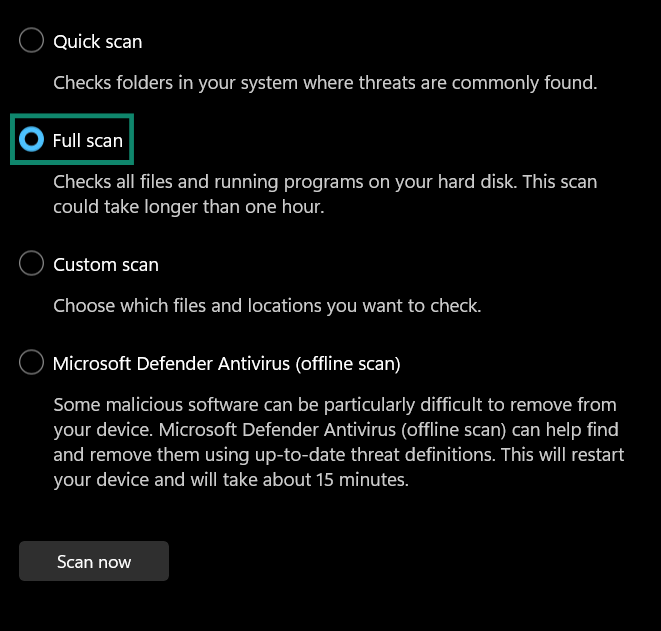
- Once the scan has completed and you get the results, you can quarantine or remove Malgent and any other malware discovered by the full scan by choosing your preferred option in the scan’s results.
Manual removal
It’s possible to remove Malgent manually, but we don’t recommend it. The process can involve deleting or modifying system files and registry keys, which can damage your device if done improperly. If you're not an experienced IT professional, it’s best to let Microsoft Defender remove Malgent. In the case that Microsoft Defender is unable to remove the infection, you may wish to seek professional assistance.
Preventing future Malgent infections
Taking proactive measures against Malgent can greatly reduce the risk of being infected. Here are some common security practices that can help protect your system.
Practice secure download and installation habits
Be cautious about what you download and install onto your computer. Malware is often bundled with legitimate-looking programs; especially in free software from unofficial websites. Only download software from the Microsoft Store or the developer’s official website to ensure you don’t accidentally install Malgent or other malware.
During installation, check for any bundled software and deselect anything you don’t want. This may help prevent the installation of potentially unwanted programs (PUPs), which can be malicious.
Please note that using illegal software "cracks" or activation tools is illegal and highly unsafe. They are frequently used to distribute trojans and other types of malware and should be avoided entirely.
Avoid phishing emails and links
Phishing and malicious links remain among the top methods for spreading malware, so it’s best to handle unsolicited emails and messages carefully. Don’t ever open attachments or click links from unknown senders. It’s also a good practice to check for common phishing red flags, such as spelling errors or urgent requests for personal information.
Keep security software updated
Malware developers constantly change their tactics to avoid detection, which makes software updates a critical defense. Ensure Windows Update is enabled and running automatically, as these updates often include patches for critical Windows security vulnerabilities.
Likewise, keep your security software, whether Microsoft Defender or a third-party antivirus, set to update its virus definitions regularly so it can recognize and block the latest malware threats.
FAQ: Common questions about Malgent
Is Trojan:Win32/Malgent a false positive?
While false positives can occur, Trojan:Win32/Malgent is a legitimate threat classification from Microsoft. If you’re unsure, you can submit the flagged file to VirusTotal to get a second opinion.
Can Malgent steal my personal data or passwords?
Malgent can download other malware specifically designed for credential and data theft. These secondary infections can steal your passwords, banking details, and other private information.
How did Malgent get on my computer?
Malgent likely got on your computer via a fraudulent email attachment, a software download from an untrustworthy source, or a visit to a malicious website.
Should I delete Malgent manually or with an antivirus?
You should always use a trusted antivirus program like Microsoft Defender. Manual removal is possible, but it’s complex and you may risk damaging your installed applications and operating system.
Can I detect Malgent without antivirus software?
Detecting Malgent without antivirus software is possible but unreliable. While you may notice symptoms like a slow PC or high CPU usage, only an antivirus scan can positively identify the specific malicious files and confirm an infection.
What’s the safest way to remove Malgent completely?
The safest way is to disconnect from the internet and run a full scan using Windows Security or a reputable third-party antivirus program. Allow the software to complete the scan and remove all found threats. If the scan fails to detect Malgent, seek professional assistance.
How do I protect my computer from Malgent in the future?
Protecting Windows devices from trojans like Malgent requires the practice of safe online habits. Be cautious of email attachments and links, and only download software from official sources. Additionally, you should ensure your Windows operating system and security software are always kept up-to-date.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN