How to limit IP address tracking for stronger online privacy
Protecting your Internet Protocol (IP) address plays an important role in maintaining your online privacy. While it doesn’t reveal your exact identity, your IP address can be used to estimate your general location and contribute to a broader profile of your online activity. This information is often collected by websites, advertisers, and analytics services for targeting and personalization.
This article explains what IP tracking is, why it’s a privacy risk, and what tools you can use to limit tracking of your IP.
What is IP address tracking?
IP addresses are the numeric labels that identify devices on the Internet, and they’re typically assigned by your internet service provider (ISP) when you connect.
IP address tracking refers to the practice of recording and analyzing your IP address as you browse, which can reveal patterns in your online behavior, location, and the devices you use. Each time you visit a website, your IP address is automatically shared with the server. As a result, web services, advertisers, and data brokers can log this information, link it to your browsing activity, and infer your general geographic location.![]()
In some cases, cybercriminals may attempt to exploit exposed IP addresses, for example, by scanning for open ports, attempting unauthorized access, or using the data to build a broader profile. While an IP address alone generally isn't enough to facilitate an attack, it can still be a useful piece of information for a threat actor.
How IP tracking works
Picture the internet as a large trail: every time you search for something along that trail, you’re taking a step. That digital footprint remains and can be used to trace your activity.
When you visit a website, your device sends a data request that includes your IP address, which acts as a return address so servers know where to send the response. The first destination is usually a Domain Name System (DNS) server, which translates the human-readable website name into the numerical IP address of the server hosting the site. The DNS server sends this information back to your device, again using your IP address as the destination. Your device can then send a request directly to the web server’s IP address, with your IP still included in each packet. Along the way, routers examine the destination IP in every packet to decide how to forward it, gradually delivering your request to the correct server.
As you load web pages, third-party scripts, ad networks, and analytics services embedded in the sites can also see your IP address. Tracking cookies may then collect additional information, such as your approximate location, browsing habits, or network details. By combining this data and linking it to your browser, data brokers and advertising companies can gradually build a behavioral profile of you over time.
Why limit IP address tracking?
As we’ve seen above, your IP address can reveal your location and browsing habits. When collected by websites, advertisers, or data brokers, it helps build detailed profiles about you, often without your knowledge. Limiting IP tracking helps protect your privacy and keeps more of your personal data under your control.
Protecting privacy and anonymity
Your IP address reveals your approximate geographical location, and it typically remains the same for days or weeks, depending on your ISP. During that time, websites and online services can use your IP to associate browsing activity across sessions, even if you're using private browsing or regularly clearing cookies.
Beyond websites, data brokers can log IP addresses to monitor activity or tie behaviors to specific users.
Limiting IP address tracking helps break these connections, making it more difficult for observers to build a coherent picture of your location, network, or online habits.![]()
Preventing tracking by advertisers
Advertisers often rely on IP addresses as a stable identifier to support techniques like geotargeting and behavioral profiling. During real-time ad auctions, which happen as a page loads, your IP address is shared alongside cookies and device data to help advertisers determine which ad to show you.
This information may be collected by multiple third parties, and even if anonymized, IP data can still help reconstruct user profiles. Digital marketing guides frequently describe IP addresses as a key tool for segmenting audiences and tracking engagement across websites.
Limiting IP address tracking helps prevent marketers from collecting one of their most reliable identifiers. Without a consistent address, it becomes more difficult to match your activity across sites, which in turn makes it harder for advertisers to build consistent behavioral profiles about you.
Defending against cyberattacks
An exposed IP address can also be a security risk. Because an IP address acts like a digital postal address, it enables communication that can be exploited by cybercriminals.
Attackers can use an unprotected IP address to scan for open ports or misconfigured services and then gain unauthorized access to networks. Distributed denial‑of‑service (DDos) attacks can be launched by directing floods of traffic at a known address, causing servers to crash or become unavailable.
Phishing campaigns are more effective when threat actors know a user’s general location, because this means they can craft emails that appear more relevant or legitimate. In some cases, an attacker with access to an IP address may attempt impersonation or conduct man‑in‑the‑middle (MITM) attacks, particularly if the target is on an unsecured network.
Limiting IP tracking may help reduce these risks by making it harder for attackers to pinpoint your location, target your network, or exploit unsecured connections.
Proven methods to limit IP address tracking
To protect your IP address, you need to combine online privacy protection software, encryption tools, and safe browsing habits. Here are some of the most effective ways to reduce IP exposure.
VPNs
A virtual private network (VPN) creates an encrypted tunnel between your device and a remote server. When you're connected, all your internet traffic is routed through this tunnel, and websites or services you access will see the VPN server’s IP address instead of your own.
This masks your real IP address and helps prevent your ISP, network administrators, or other third parties from monitoring your online activity or tracking your approximate location. Because your traffic is encrypted, it's also protected from potential eavesdropping on public or unsecured networks, such as public Wi-Fi.![]()
However, not all VPNs offer the same level of protection. Look for a service that has a strict no-logs policy, meaning it doesn’t store records of your activity. For additional privacy, features like dynamic IP rotation, which regularly changes your visible IP address, can make it harder for observers to link your sessions together.
ExpressVPN also offers the Threat Manager tool, which helps block trackers that are known to engage in harmful behaviour. This extra layer of protection can help prevent your IP and other data from being acquired by malicious third parties.
Tor browser for anonymity
The Tor network is a free, open-source system designed to enhance online privacy. It works by routing your traffic through a random series of three volunteer-run servers (called "nodes" or "relays"). Each relay only knows the previous and next hop, and your data is encrypted multiple times (once for each relay in the path). This makes it difficult for websites, ISPs, or other observers to trace your online activity back to your real IP address or location.
However, there are important privacy considerations, especially in the context of our topic. Even though the websites you visit while using Tor can’t track you using your IP address, the entry node (the first of the three volunteer-run servers) can see it. Moreover, there is no way for you to know who is running the entry node and if it’s compromised. That’s why it’s a good idea to use Tor alongside a reliable VPN (and connect to the VPN first) rather than instead of it.
Cloud PCs and virtual desktops
Another way to mask your IP address is to use a cloud PC or virtual desktop. When you connect to a cloud‑based workstation, your traffic is routed through that remote system. Connecting to a virtual desktop routes your traffic through the remote system’s IP address, masking your real address.
Because cloud providers, such as Shadow, Amazon Workspaces, or Microsoft Azure, typically offer servers from multiple regions and use dynamic IP allocation, your traffic will appear to originate from different areas or from shared IP pools. This can make it harder for third parties to track you.
While this method isn't as secure or private as using a VPN, it can still be a useful tool, especially for remote work or running potentially risky tools in a sandboxed environment. You can configure a VPN within a virtual desktop for added privacy, but this setup can be complex and may lead to networking issues, particularly with DNS resolution or routing conflicts.
Dynamic IP address rotation
Dynamic IP address rotation changes your IP periodically, making it more difficult to link your online actions over time.
Some VPN services, like ExpressVPN, assign you a different IP address each time you access a server or website. This rotation helps obscure patterns in your browsing behavior.
Outside of VPNs, ISPs often assign dynamic IP addresses using Dynamic Host Configuration Protocol (DHCP). Your IP might also change when switching between networks (for example, moving from Wi-Fi to mobile data) since mobile networks often use large pools of dynamic IPs.
While IP rotation increases anonymity, it doesn't encrypt your traffic. For true privacy, it should be used alongside a VPN.
iCloud Private Relay (for Apple devices)
iCloud Private Relay is an Apple feature that provides a built-in method to limit IP exposure on your iOS or Mac device. Private Relay is available to subscribers of iCloud+, and it encrypts your Safari traffic before sending it through two separate internet relays.
The first relay assigns an anonymous IP address that approximates your region, while the second decrypts the address of the website you’re visiting and forwards your request. This design ensures that no single relay knows both who you are and where you’re going.
However, unlike a VPN, iCloud Private Relay only encrypts your Safari traffic and always assigns you an IP address from your region.
Protecting your IP address with firewall and security rules
A firewall acts as a barrier between your device and the internet by monitoring and filtering traffic based on predefined rules. While concealing your IP address protects you from tracking, configuring a firewall to reject traffic from unknown sources reduces the risk of attacks directed at your IP address. Additionally, IP whitelisting can restrict access to sensitive resources so that only authorized addresses can connect.
Step-by-step guide to hide your IP address
Here are some practical steps you can take to mask your IP address or dissociate it from your search queries. Depending on your browser and device, we’ll take you through instructions to:
- Encrypt your DNS requests: Prevents third parties from linking your IP address to the websites you visit by hiding your DNS lookups.
- Block unauthorized traffic: Stops unapproved connections that could expose your IP address to unwanted parties.
- Disable ad tracking: Reduces the ability of advertisers to link your IP to your browsing habits.
- Hide your IP from trackers, apps, and email senders: Masks your real IP address to prevent location and identity tracking.
- Prevent Web Real-Time Communication (WebRTC) leaks: Closes a browser loophole that could expose your real IP.
- Block cross-site trackers: Stops third-party scripts from following you across sites using your IP and other identifiers.
Windows
Windows includes built-in tools to encrypt DNS requests and block unauthorized traffic. Enabling these features helps prevent your ISP and outside observers from seeing the websites you visit or accessing your network directly.
- Open Settings, then select Network & Internet.
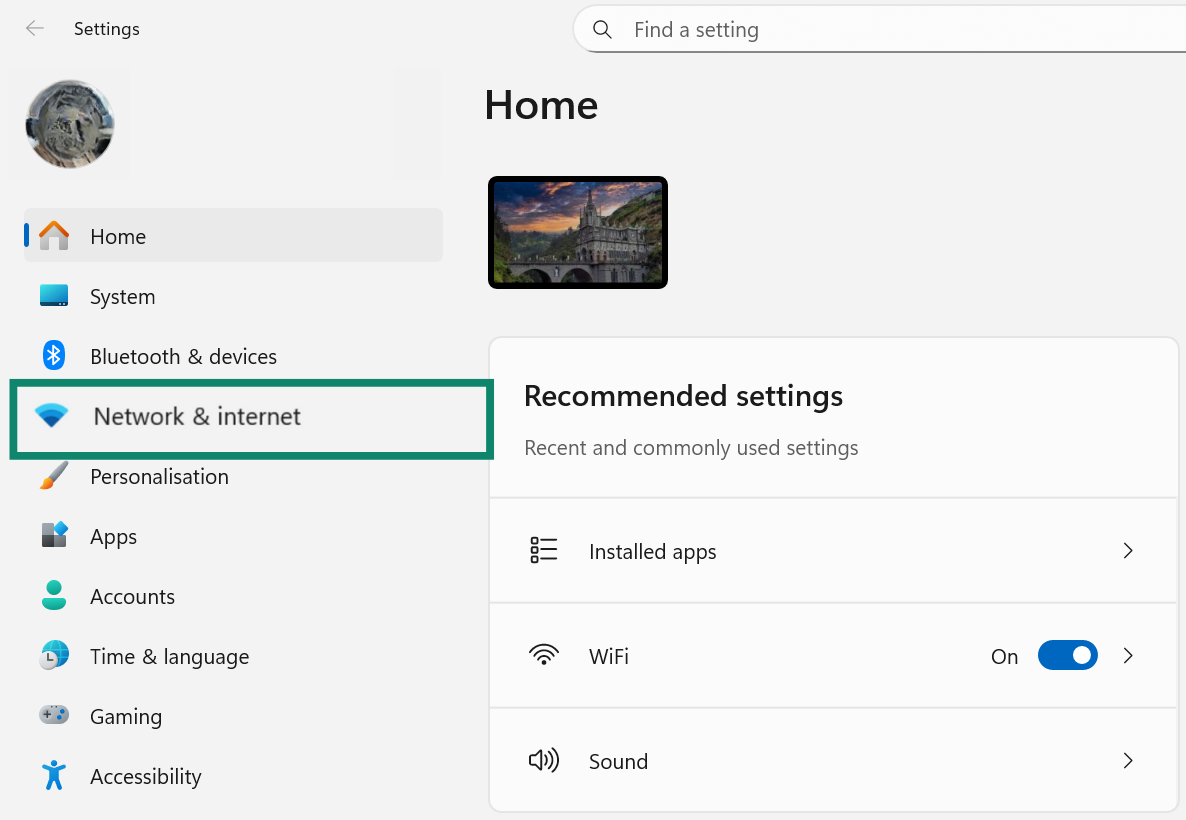
- Find your internet connection under either WiFi or Ethernet and click on your connection.
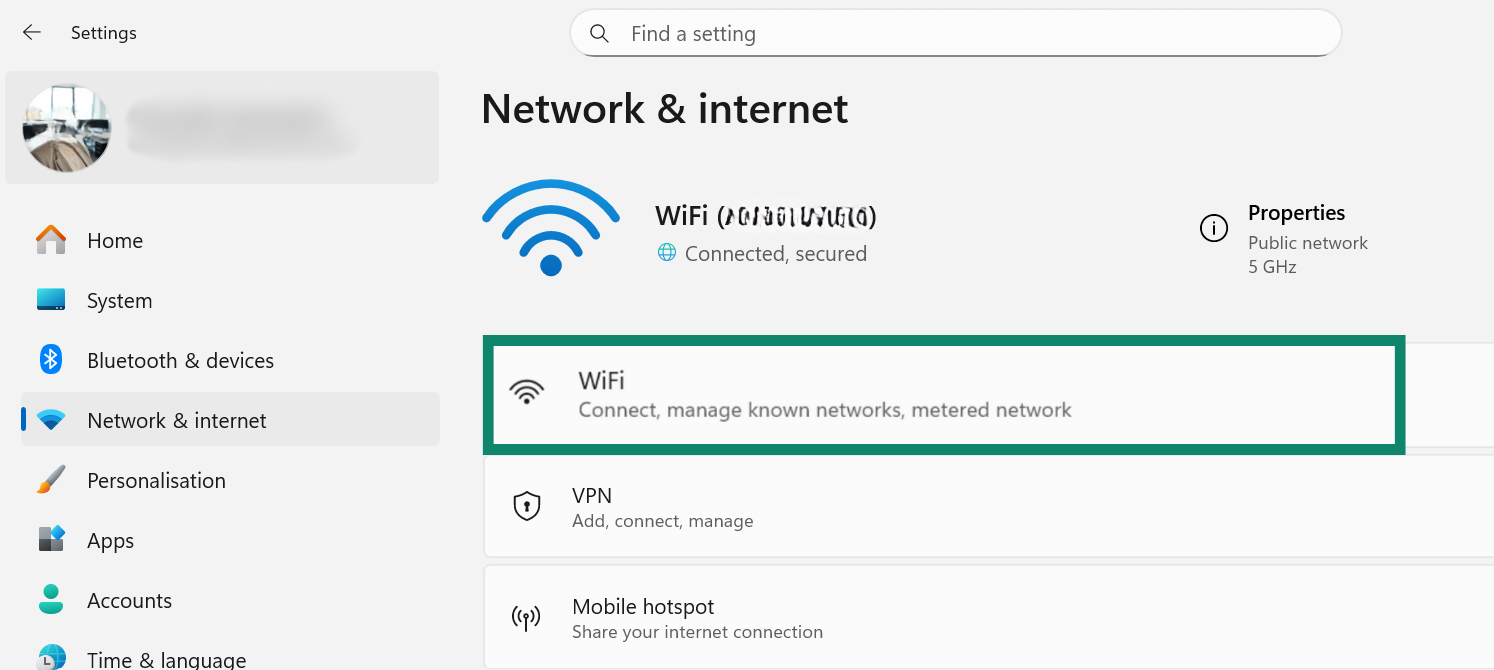
- Scroll to IP assignment and select Edit.
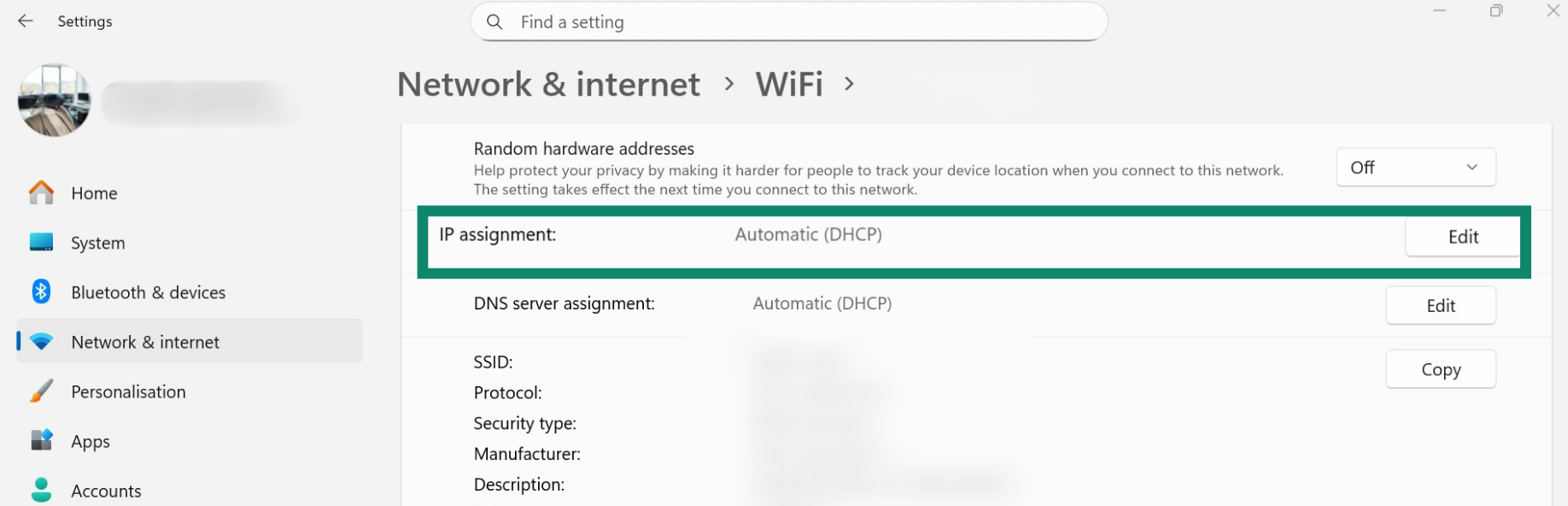
- Choose Manual.
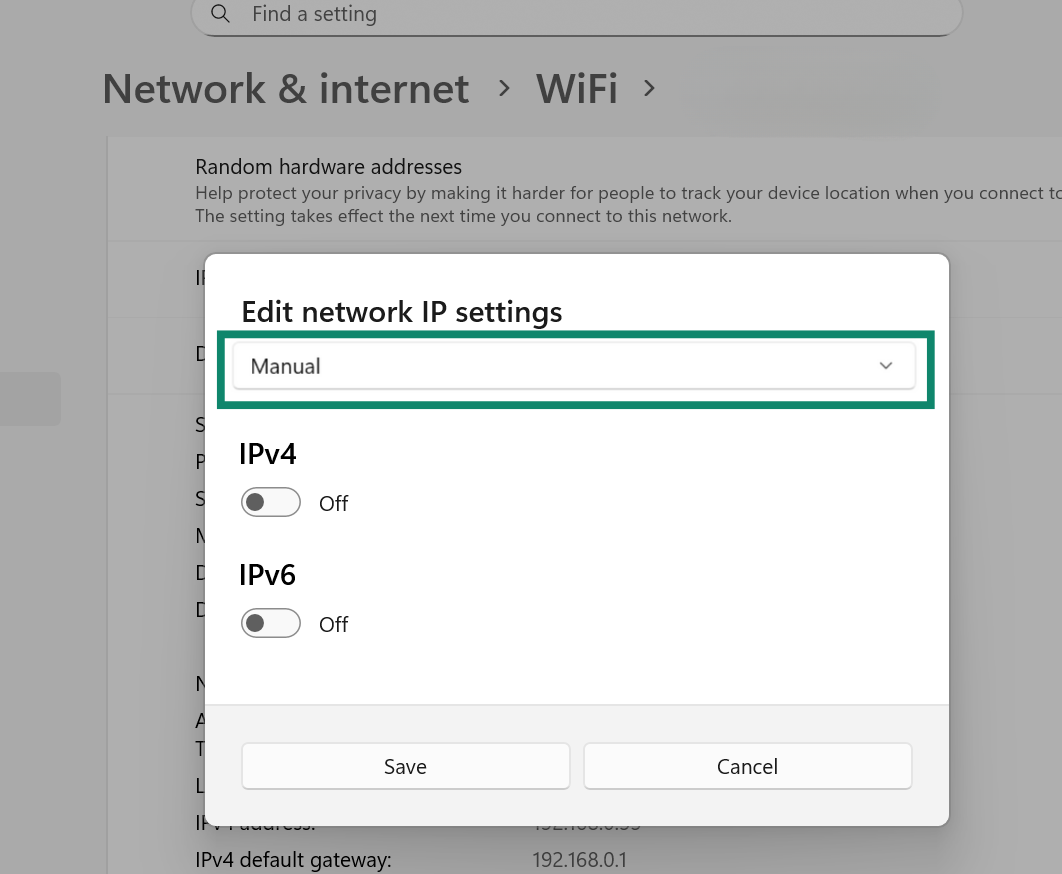
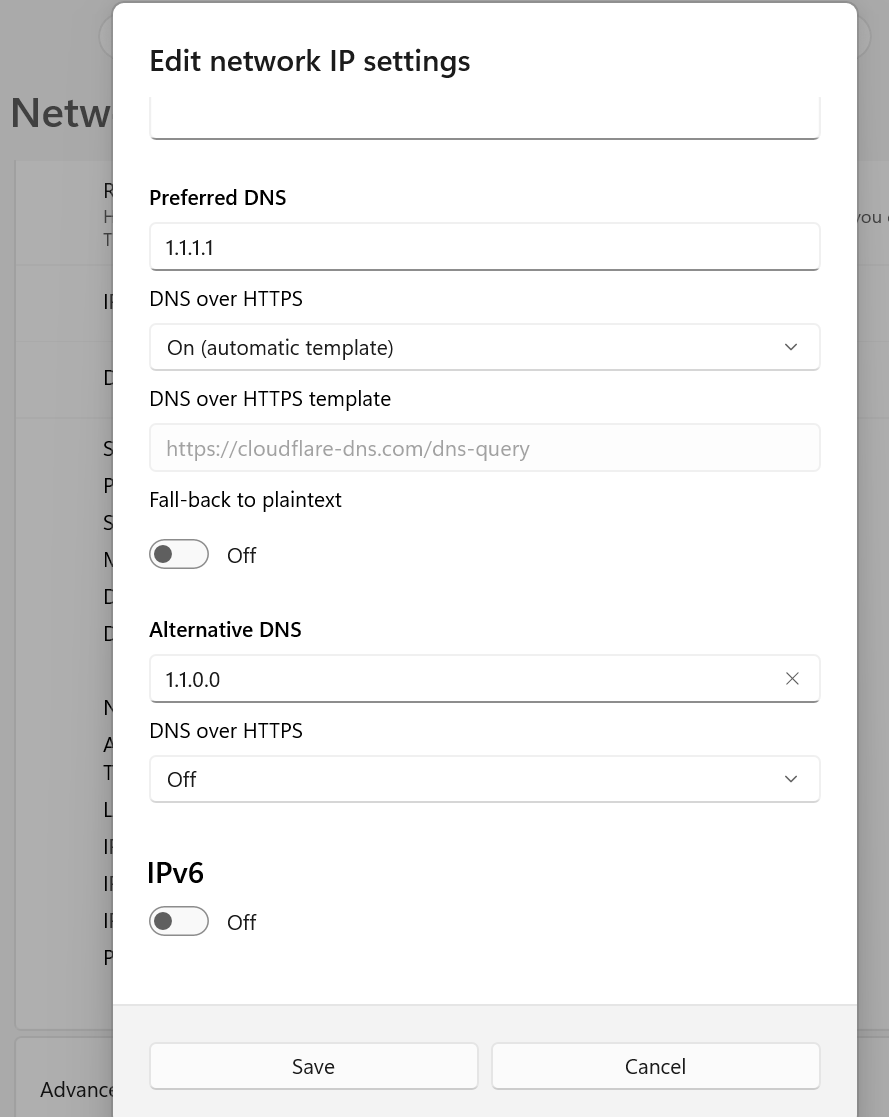
- Enable IPv4, then fill in the details for a trusted provider such as Cloudflare or Google.
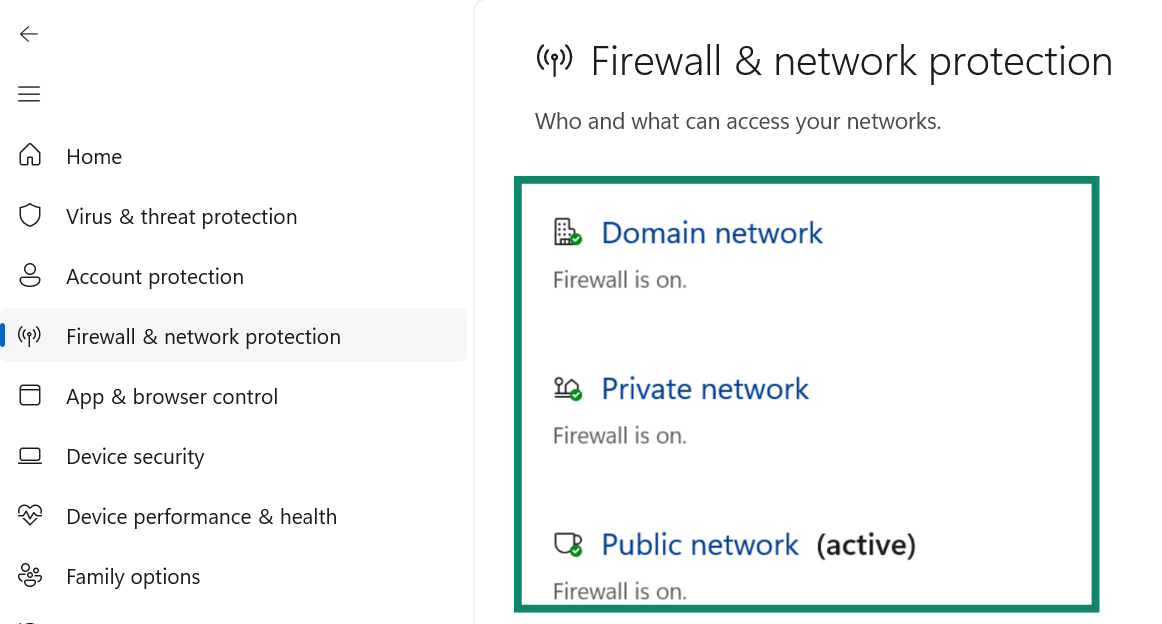
- Exit this page and open Windows Security, then select Firewall & network protection.
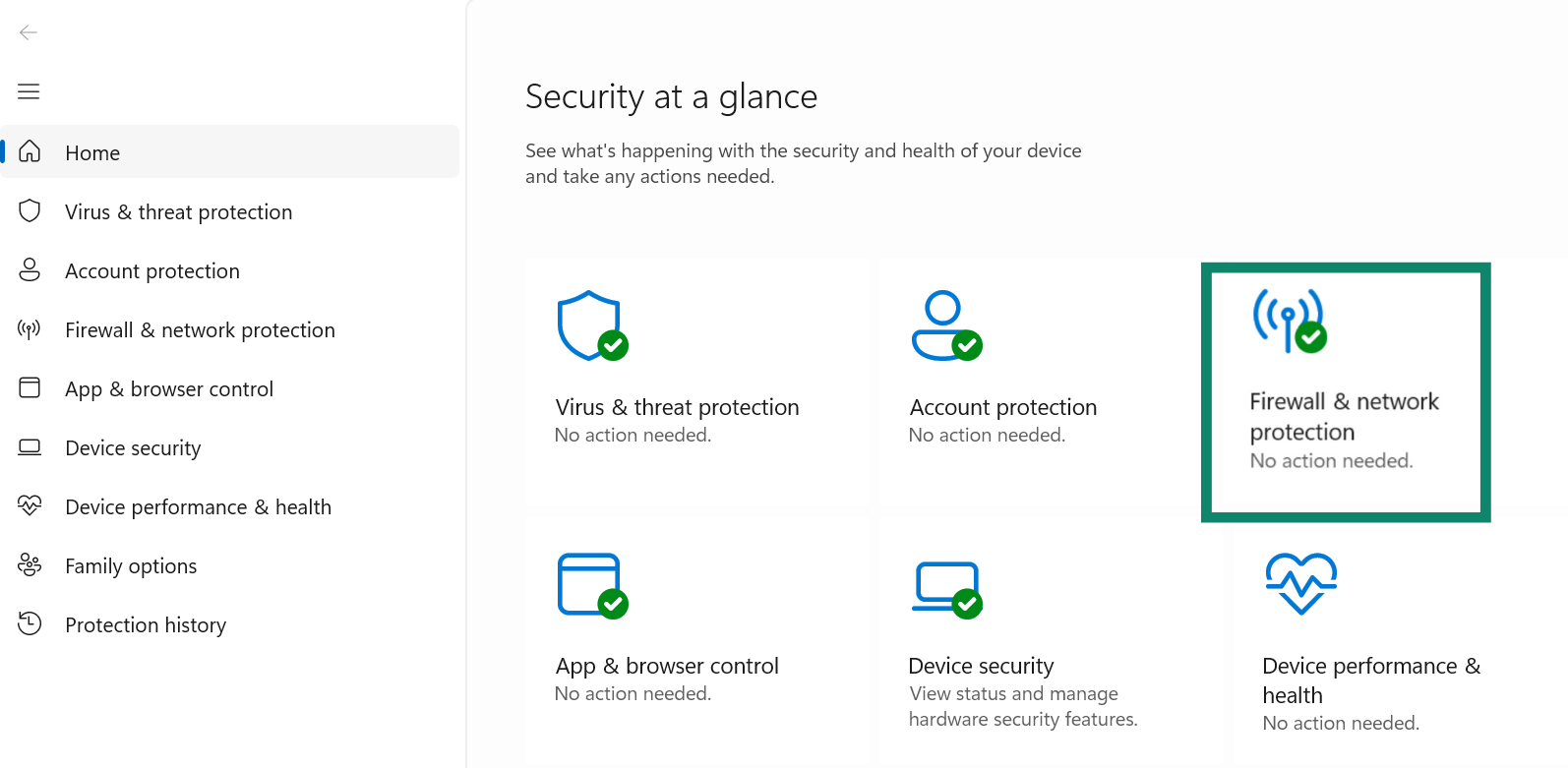
- Make sure Microsoft Defender Firewall is turned on for all network types. This blocks unauthorized access attempts targeting your IP address. If it isn’t active, you can toggle it on.
Mac
Mac systems allow you to hide your IP address and encrypt DNS lookups directly within your settings. Turning these on ensures advertisers and ISPs can’t associate your browsing with your real IP address.
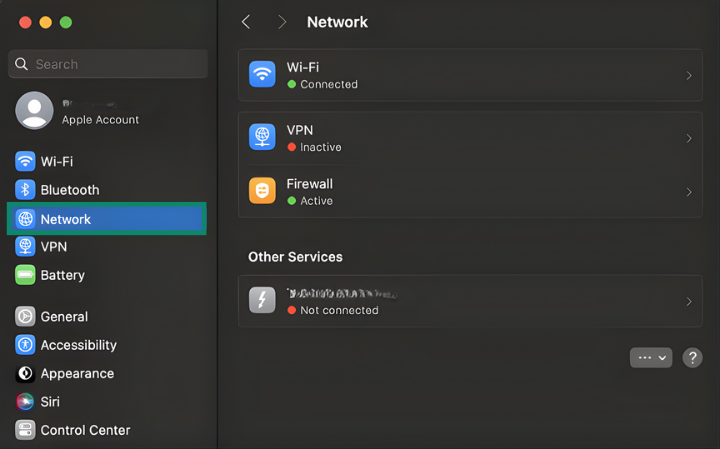
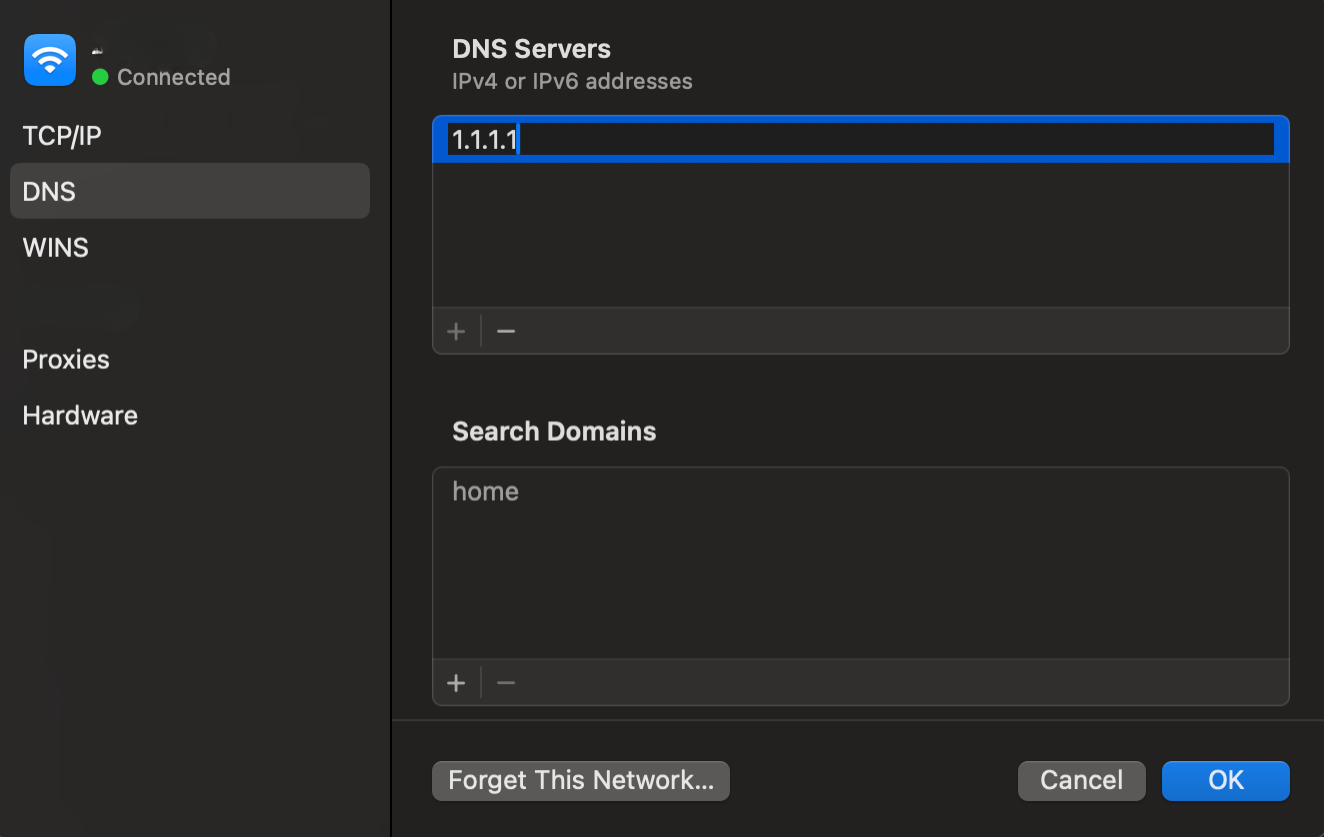
- Open System Settings and select Network.
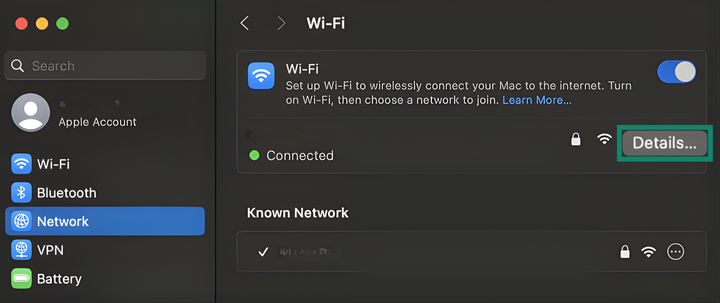
- Choose your active connection and click Details.
- Select DNS and then click the + button to add a new IP.
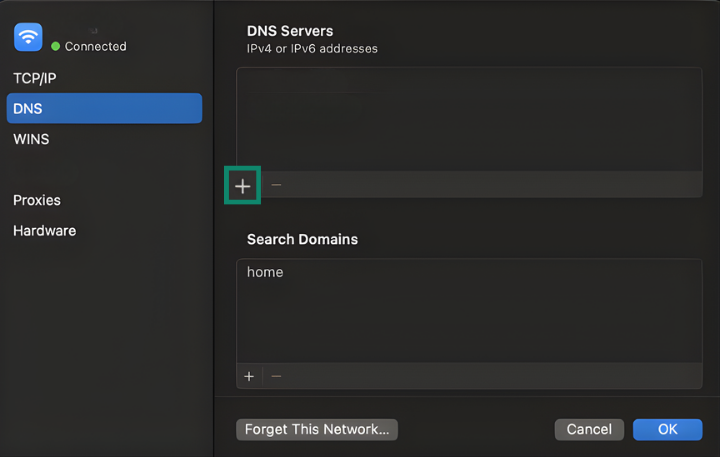
- Add a secure resolver such as 1.1.1.1 or 8.8.8.8 to encrypt your DNS traffic.
Android
Android devices can encrypt DNS queries and disable ad tracking to reduce how much of your data is tied to your IP address. These options make it harder for advertisers and ISPs to monitor your activity.
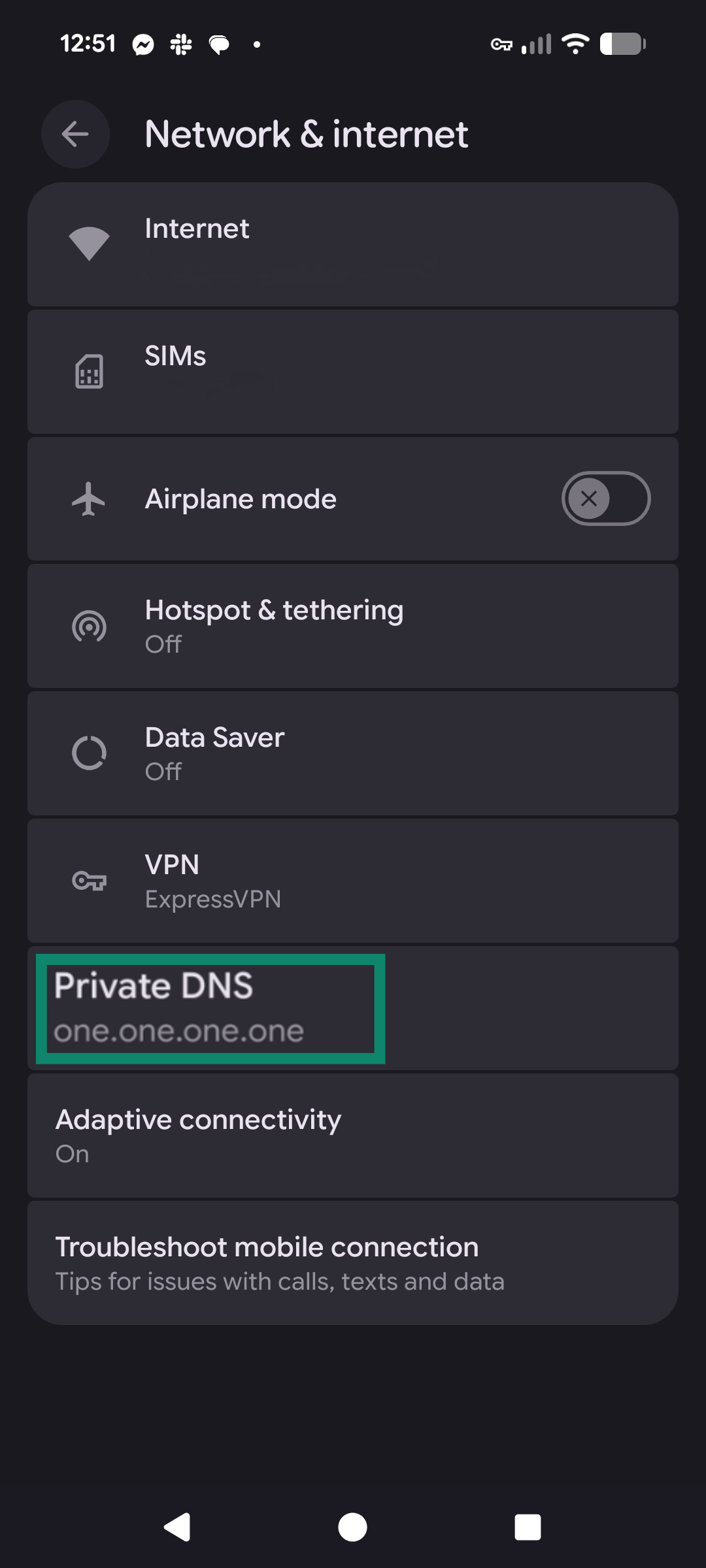
- Open Settings, select Network & Internet, and tap Private DNS. (Alternatively, you can search your Settings for “Private DNS”.)
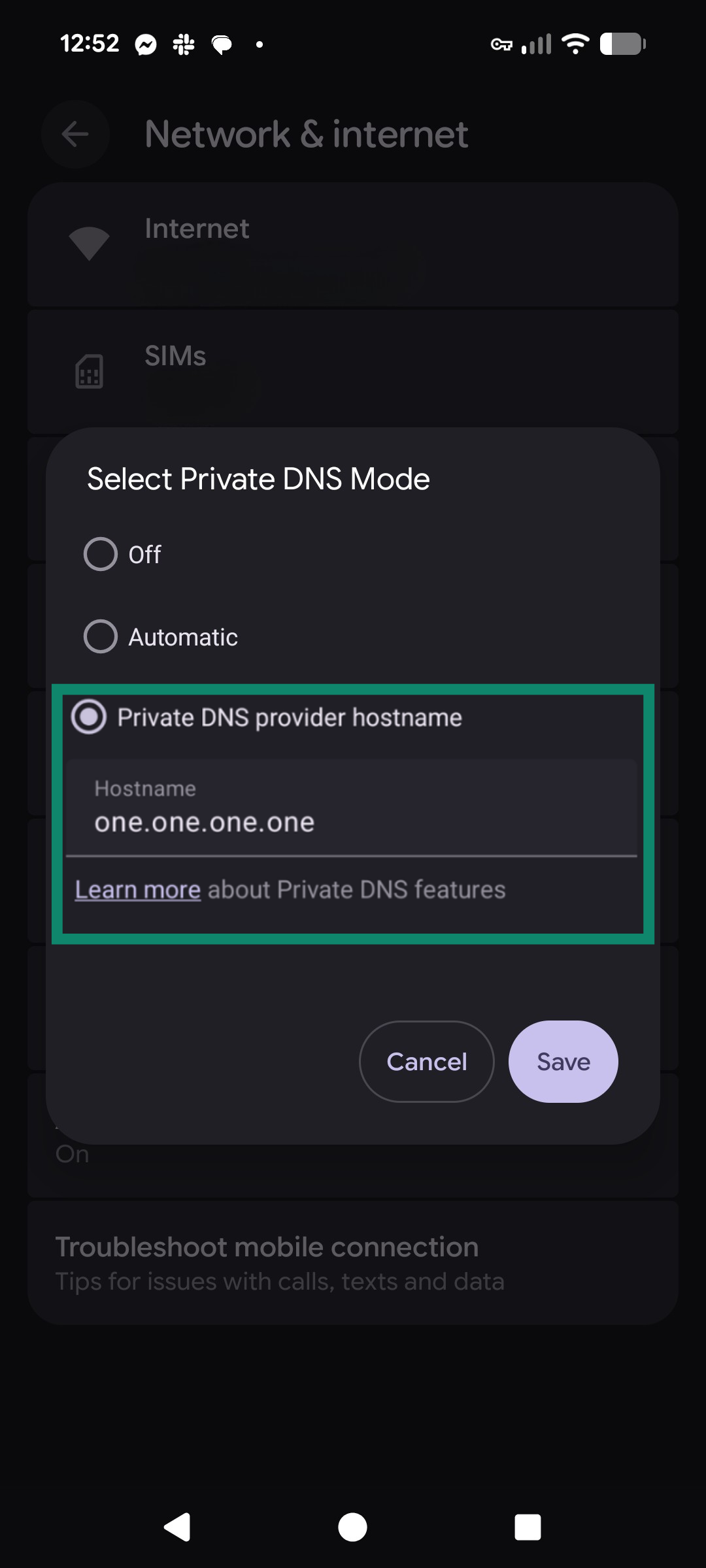
- Choose Private DNS and enter a trusted resolver such as Google or Cloudflare's public DNS. Confirm your DNS by clicking Save.
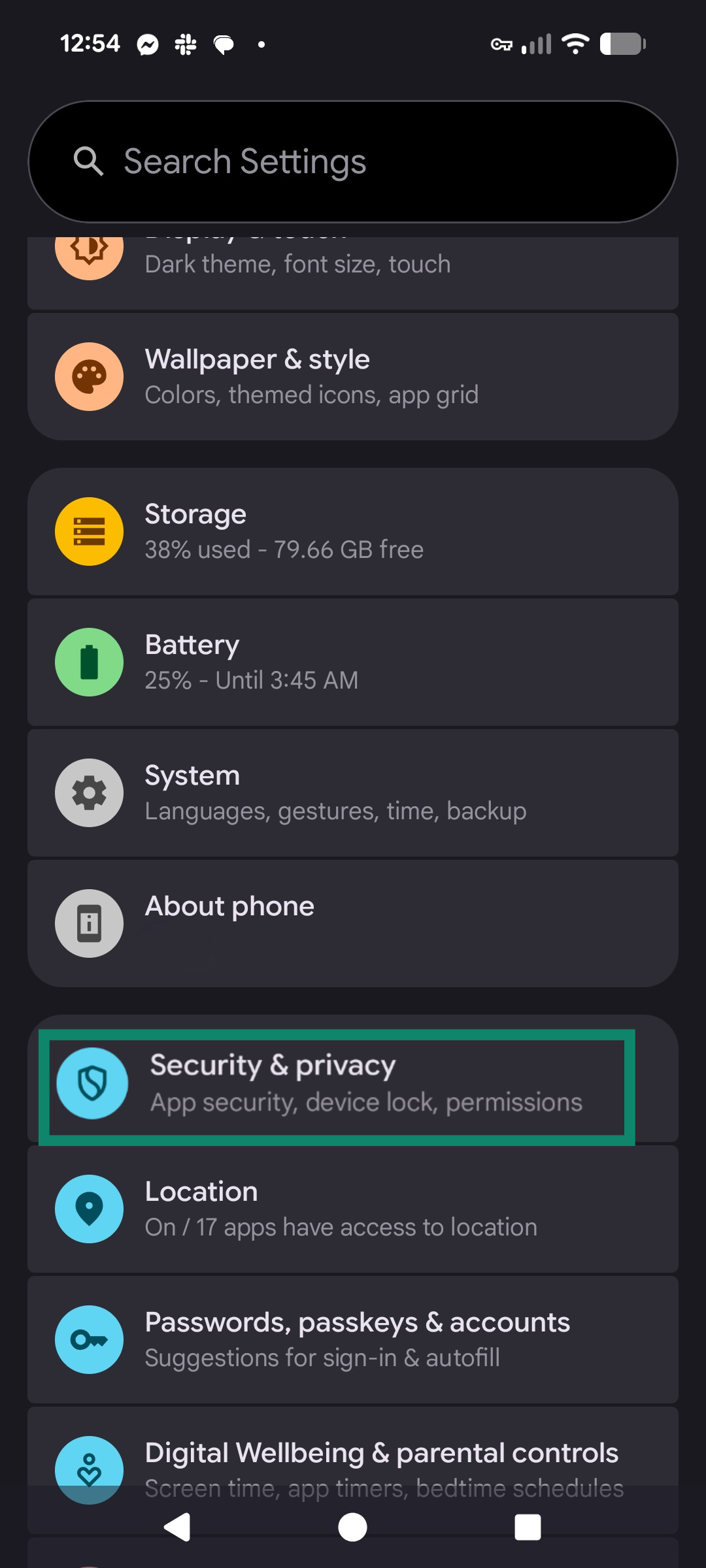
- To limit ad tracking, open Settings and select Security & privacy.
- Open Privacy controls and choose Ads.
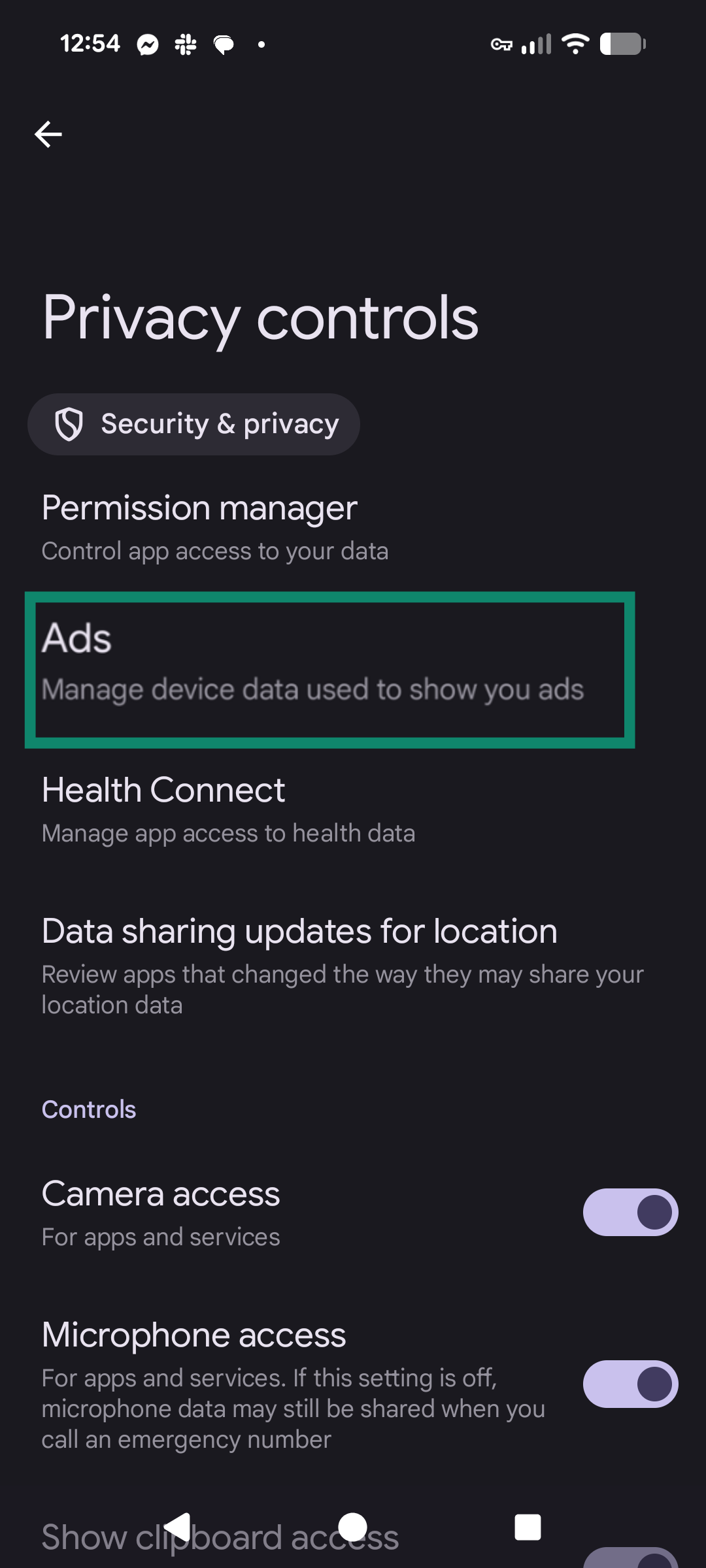
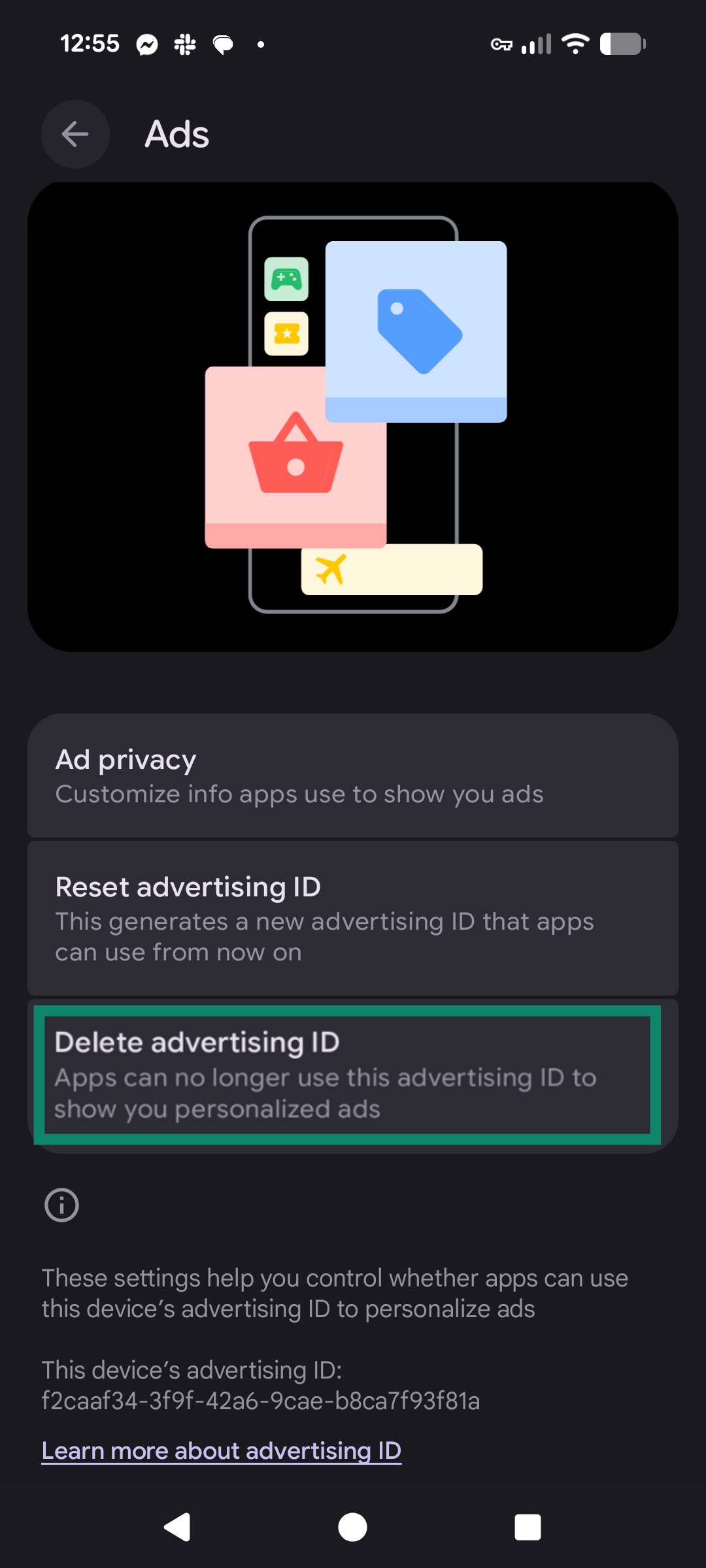
- Toggle Delete advertising ID and confirm your choice.
iOS
Apple devices include multiple settings that hide your IP from trackers, apps, and email senders. These steps prevent websites and advertisers from linking your identity across platforms.
- Open Settings and select Privacy & Security.
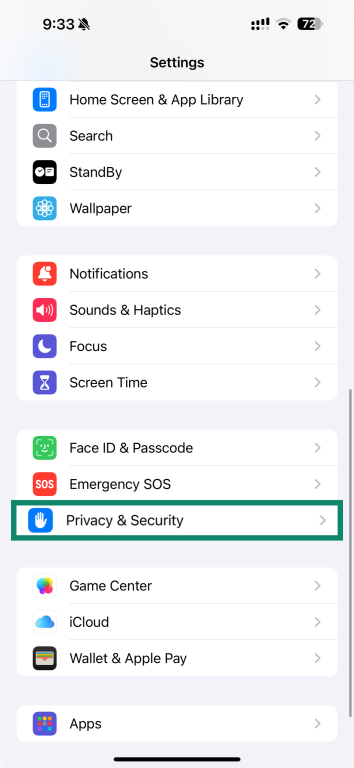
- Open Tracking.
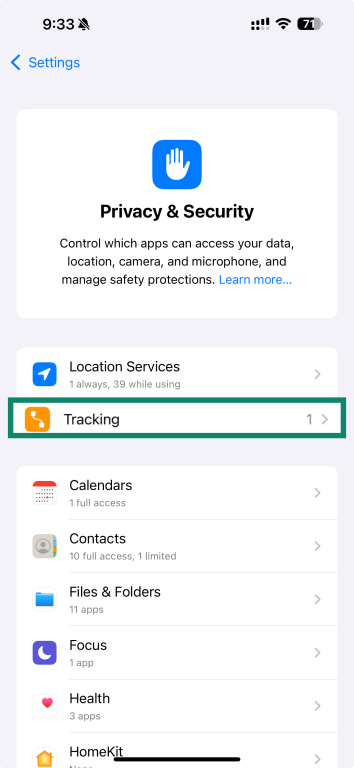
- Disable Allow Apps to Request to Track. You’ll need to confirm your choice.
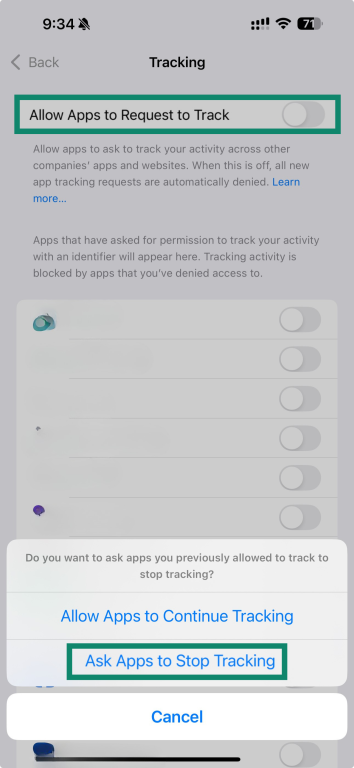
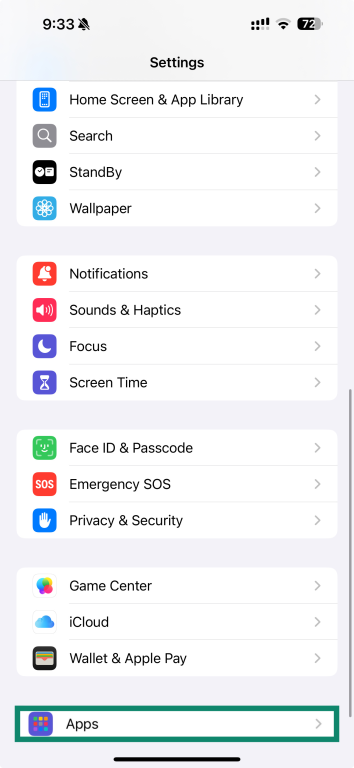
- Go back to your settings menu, choose Apps, then select Mail.
- Choose Privacy Protection.
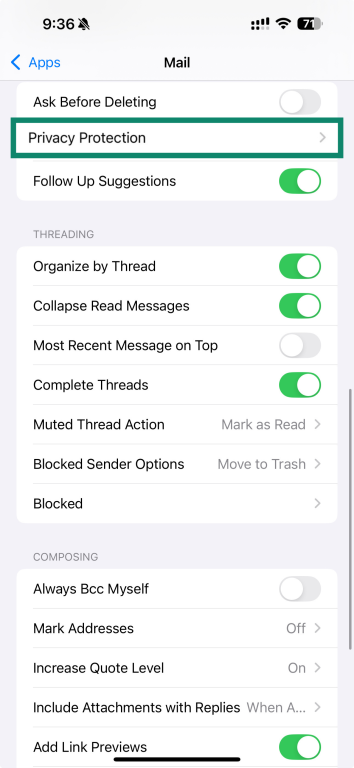
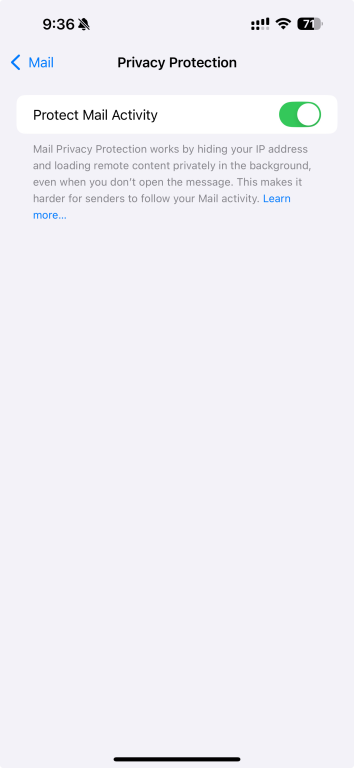
- Enable Protect Mail Activity. This hides your IP when loading remote content in emails.
Browsers
Google Chrome
Chrome lets you encrypt DNS lookups, which stops your ISP and public networks from tracking your browsing history.
- Open Settings, then select Privacy and Security.
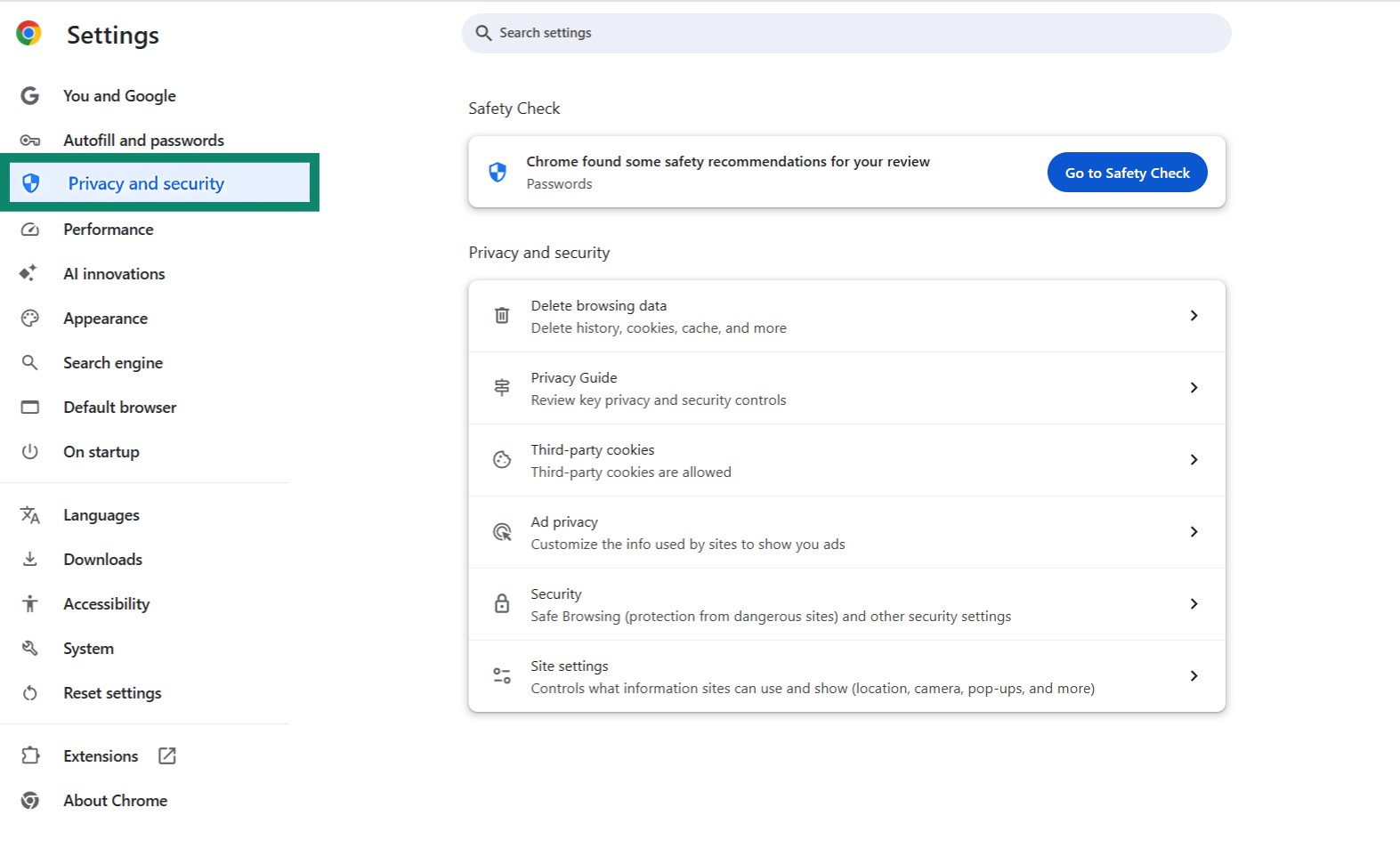
- Choose Security.
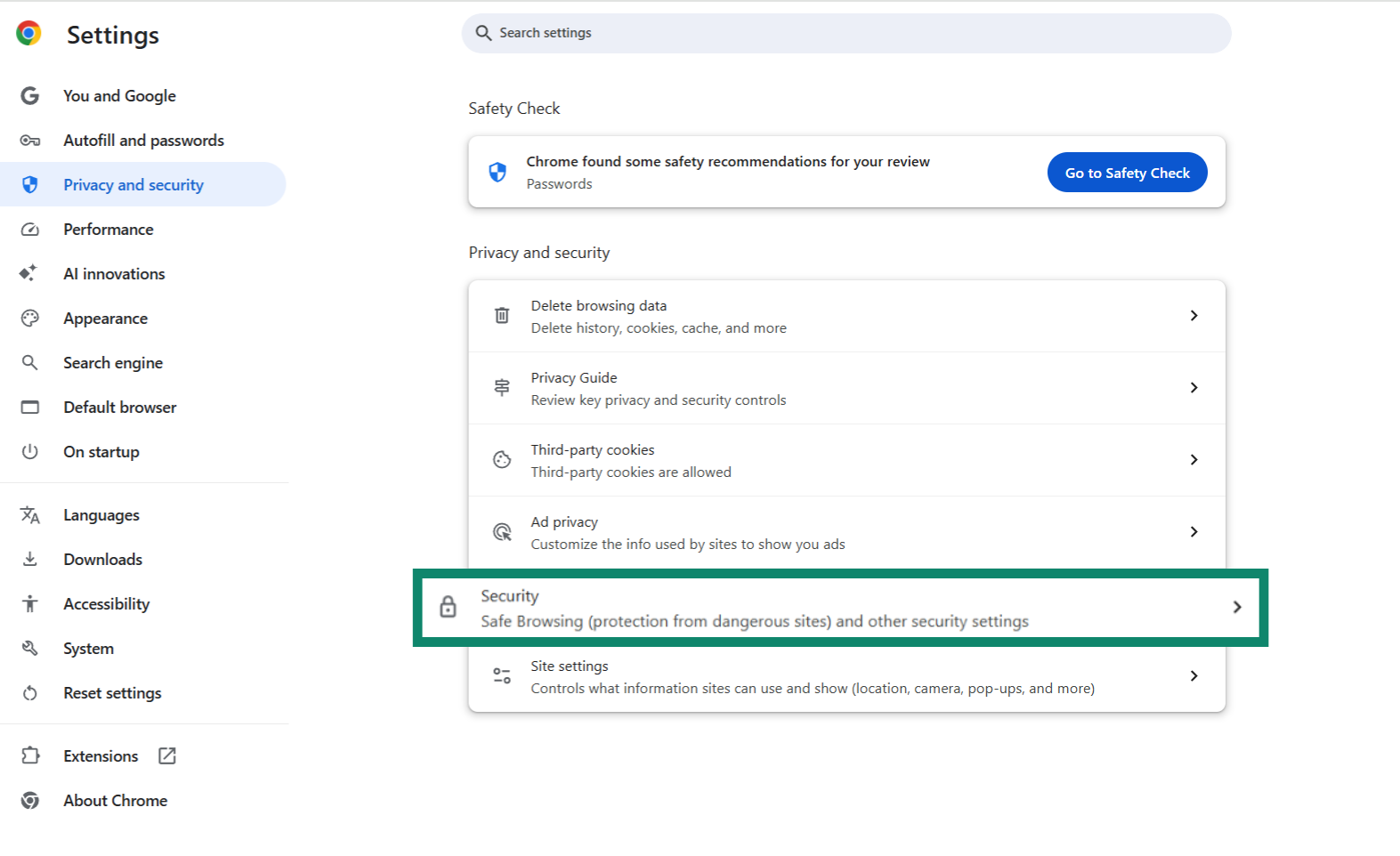
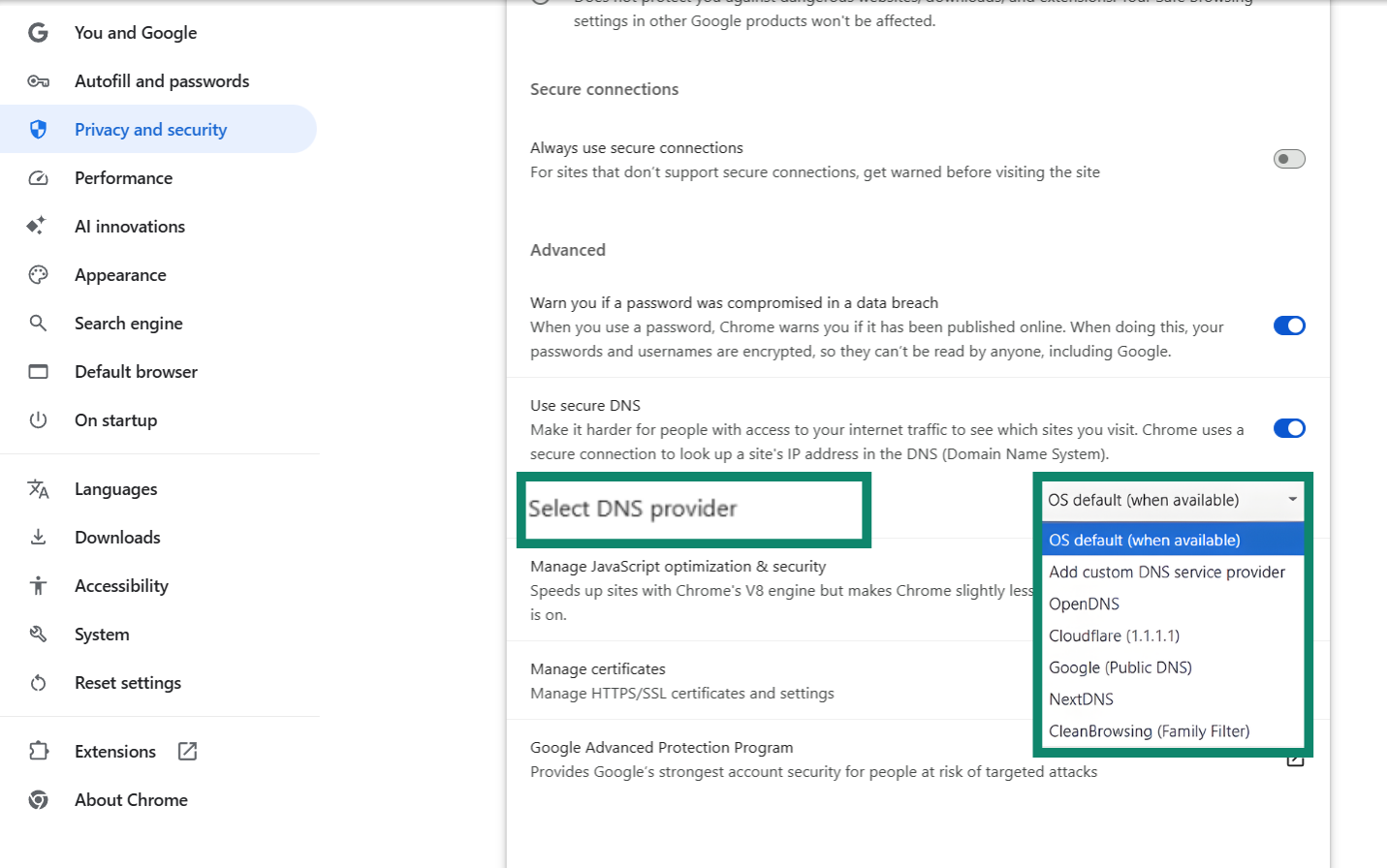
- Scroll to Use secure DNS, toggle it on, and select a provider such as Cloudflare or Google Public DNS.
Firefox
Firefox offers several tools to block IP-based tracking and isolate your browsing sessions. Enabling these features prevents data brokers and advertisers from following you across sites.
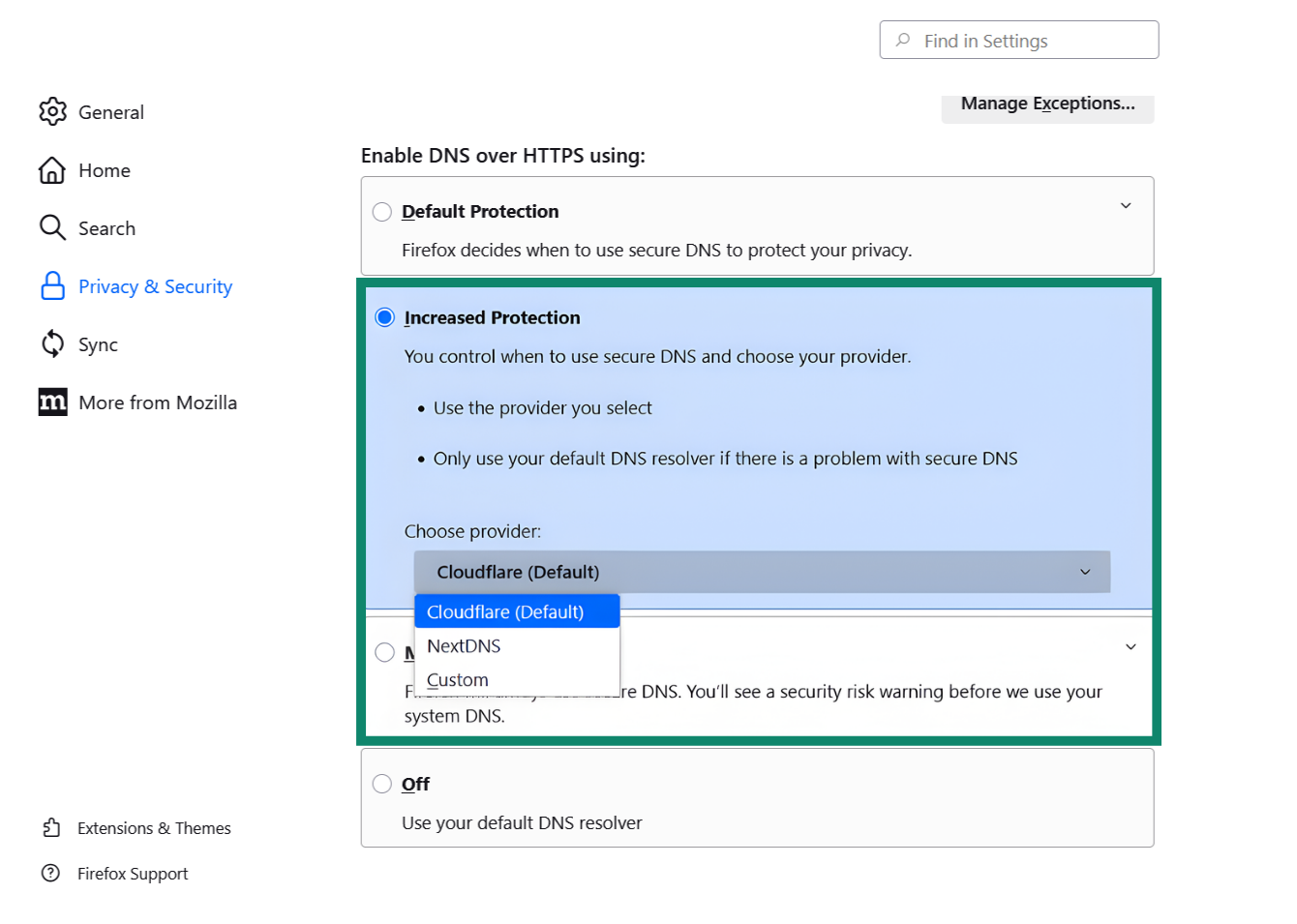
- Type about:preferences in the address bar or open Settings. Next, open Privacy & Security.
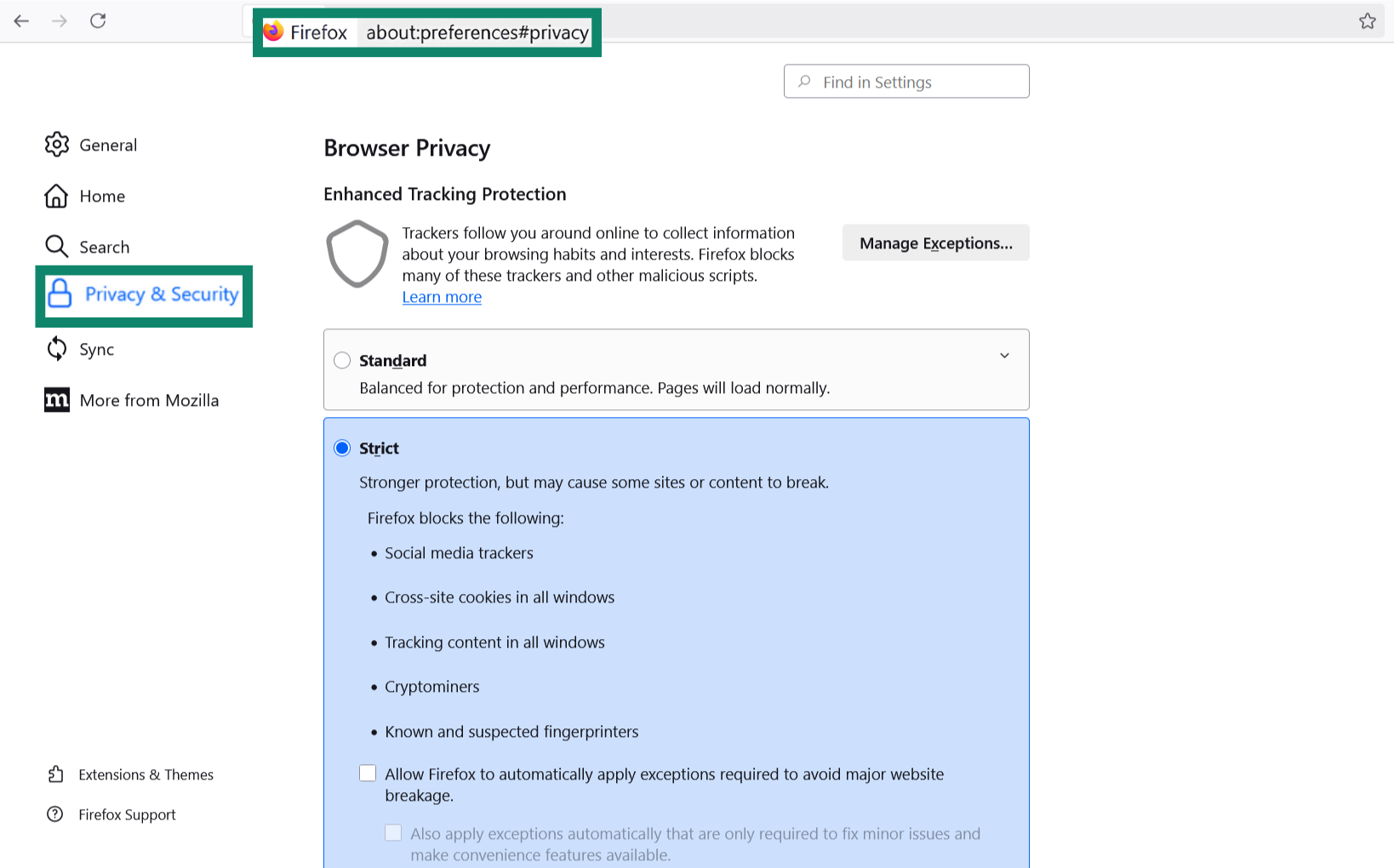
- Scroll to DNS over HTTPS, enable it, and select a trusted provider.
- To prevent WebRTC leaks, type about:config.
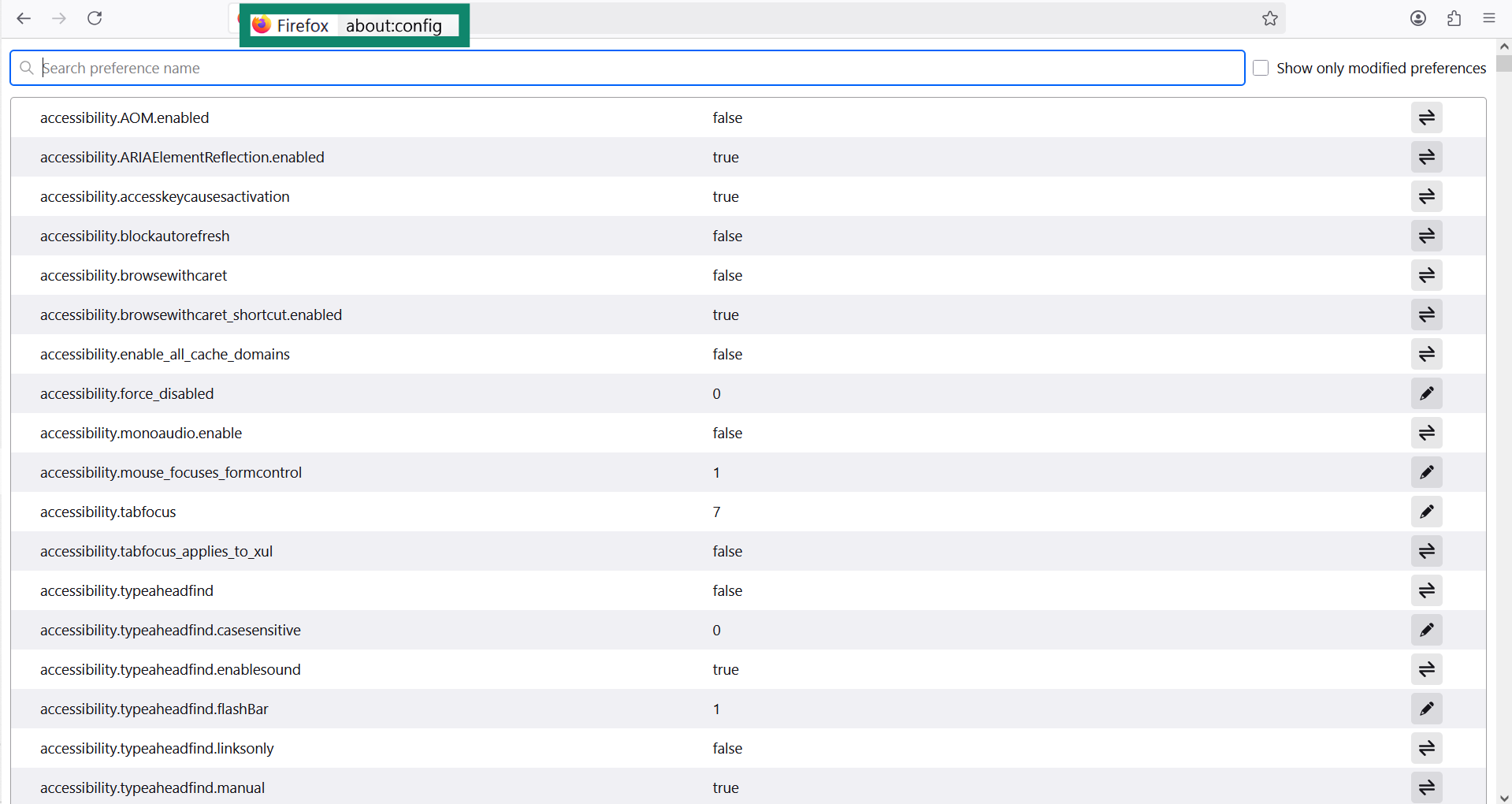
- Search for media.peerconnection.enabled and set it to false.
- If you have technical expertise, you could also install Firefox Multi-Account Containers from the Add-ons store to isolate tabs and limit cross-site tracking tied to your IP.
Safari
Safari includes built-in options to hide your IP and encrypt browsing activity. These settings prevent advertisers and analytics tools from tracking your identity across websites.
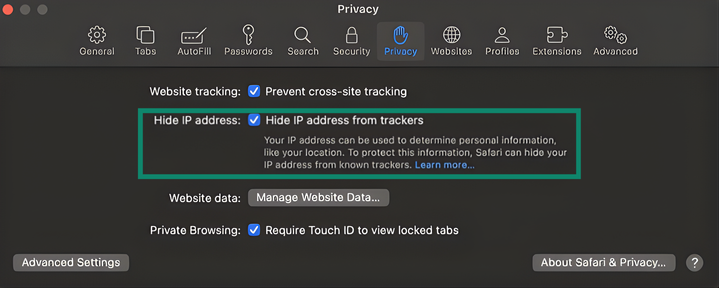
- Open Safari, select Settings, then Privacy.
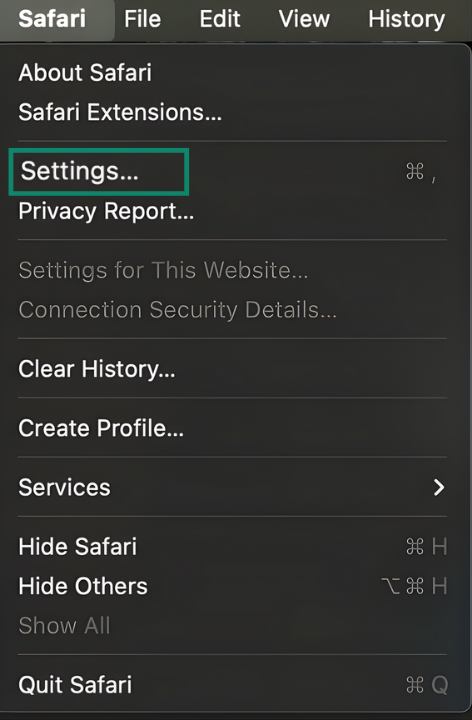
- Check Hide IP address from trackers.
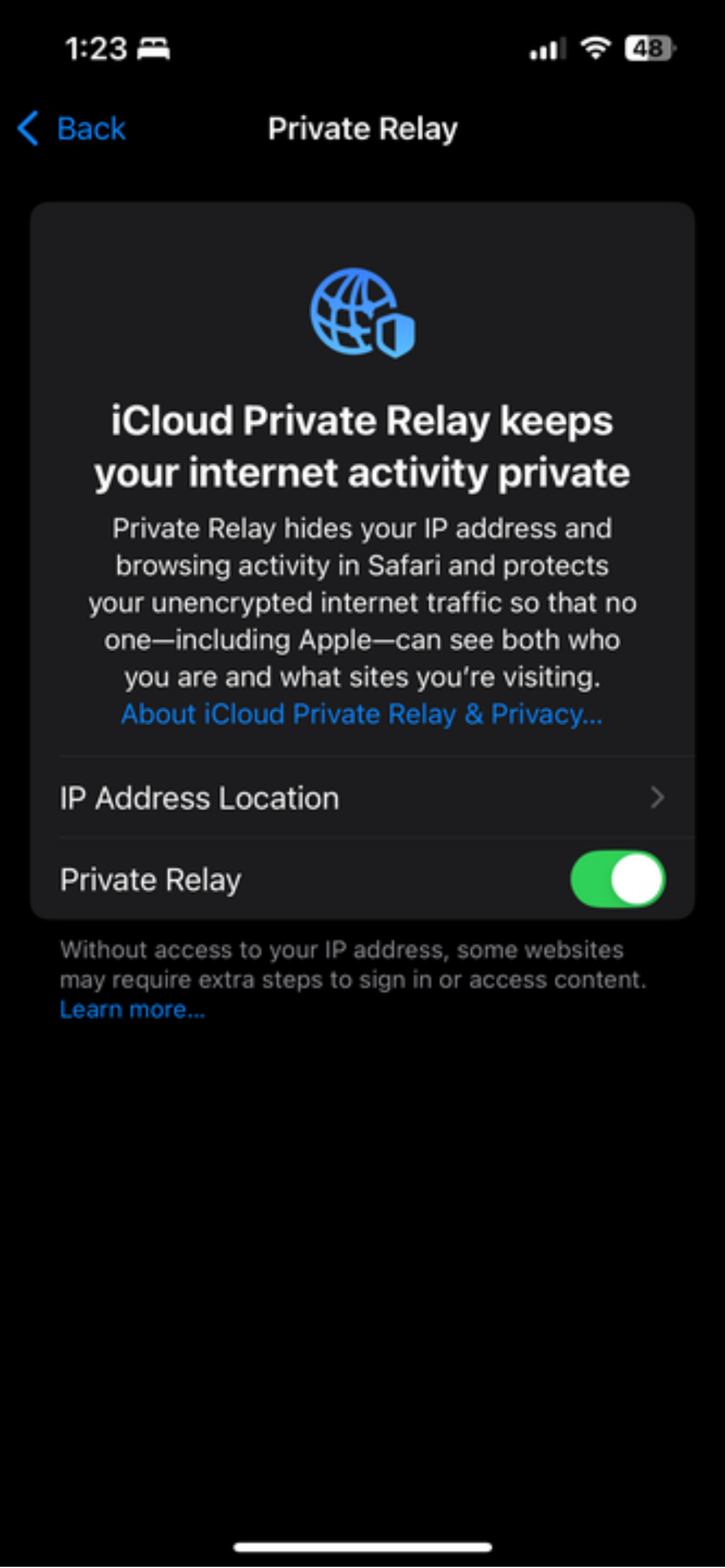
- If you have iCloud+, open System Settings and select Apple ID.
- Open iCloud.
- Find and open Private Relay.
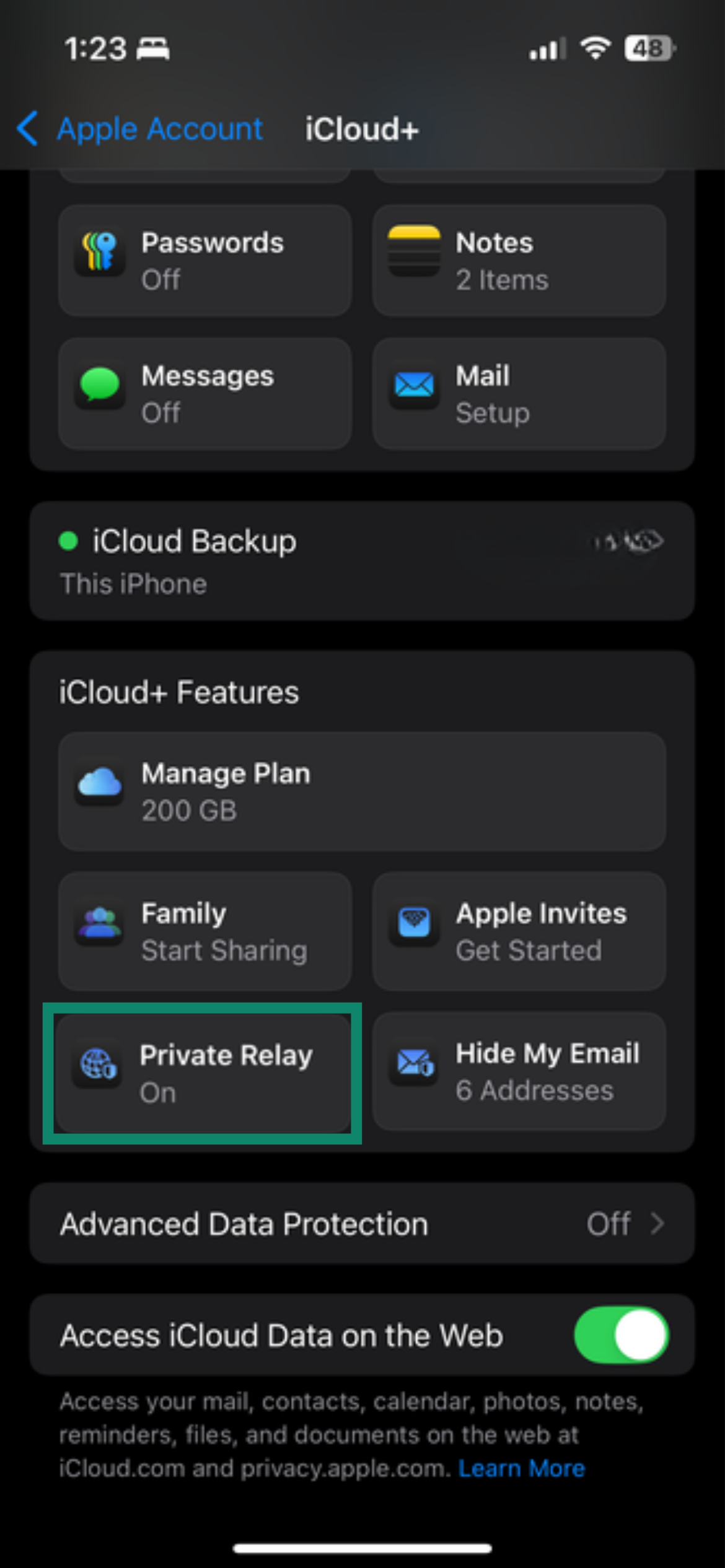
- Enable Private Relay.
Edge
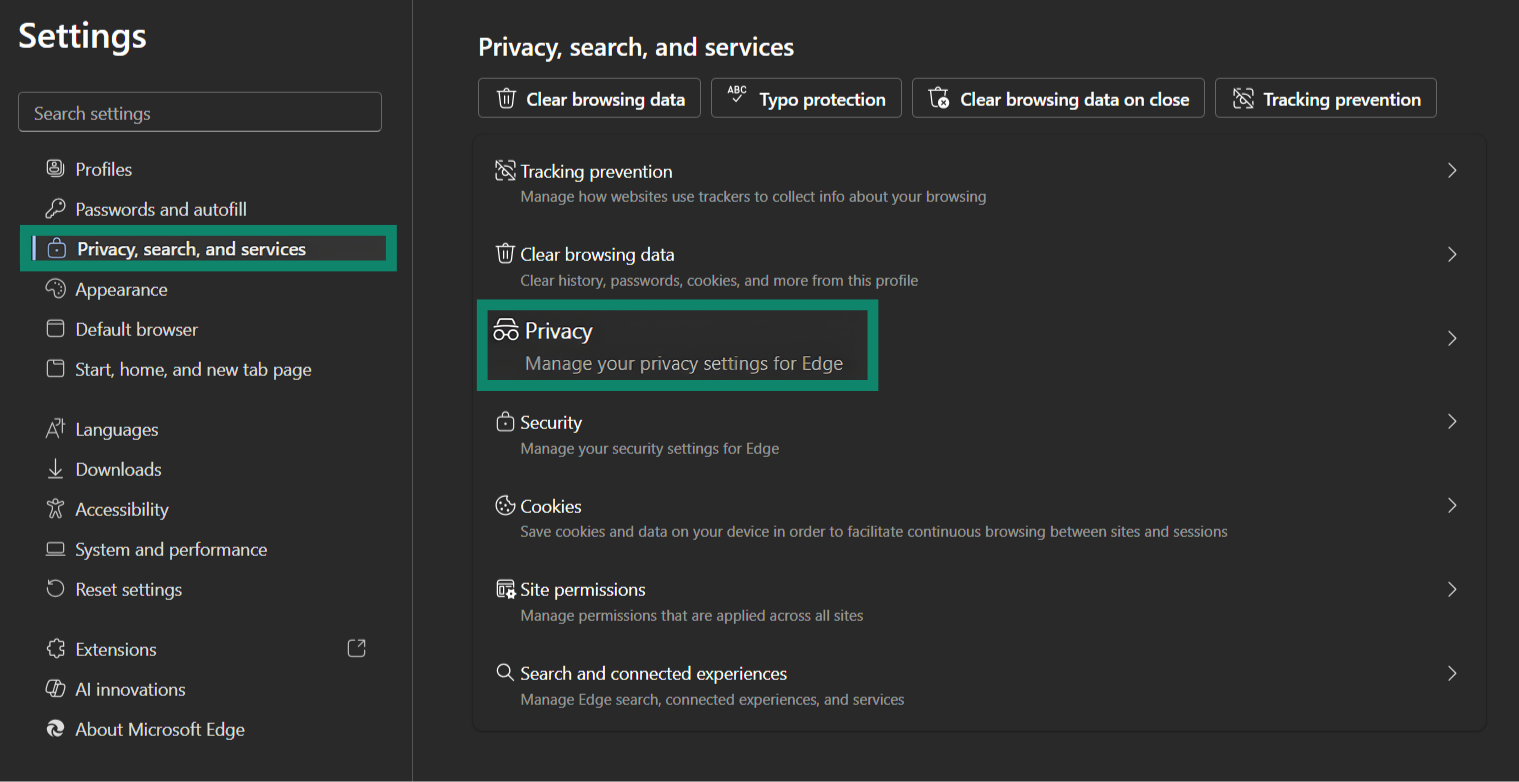
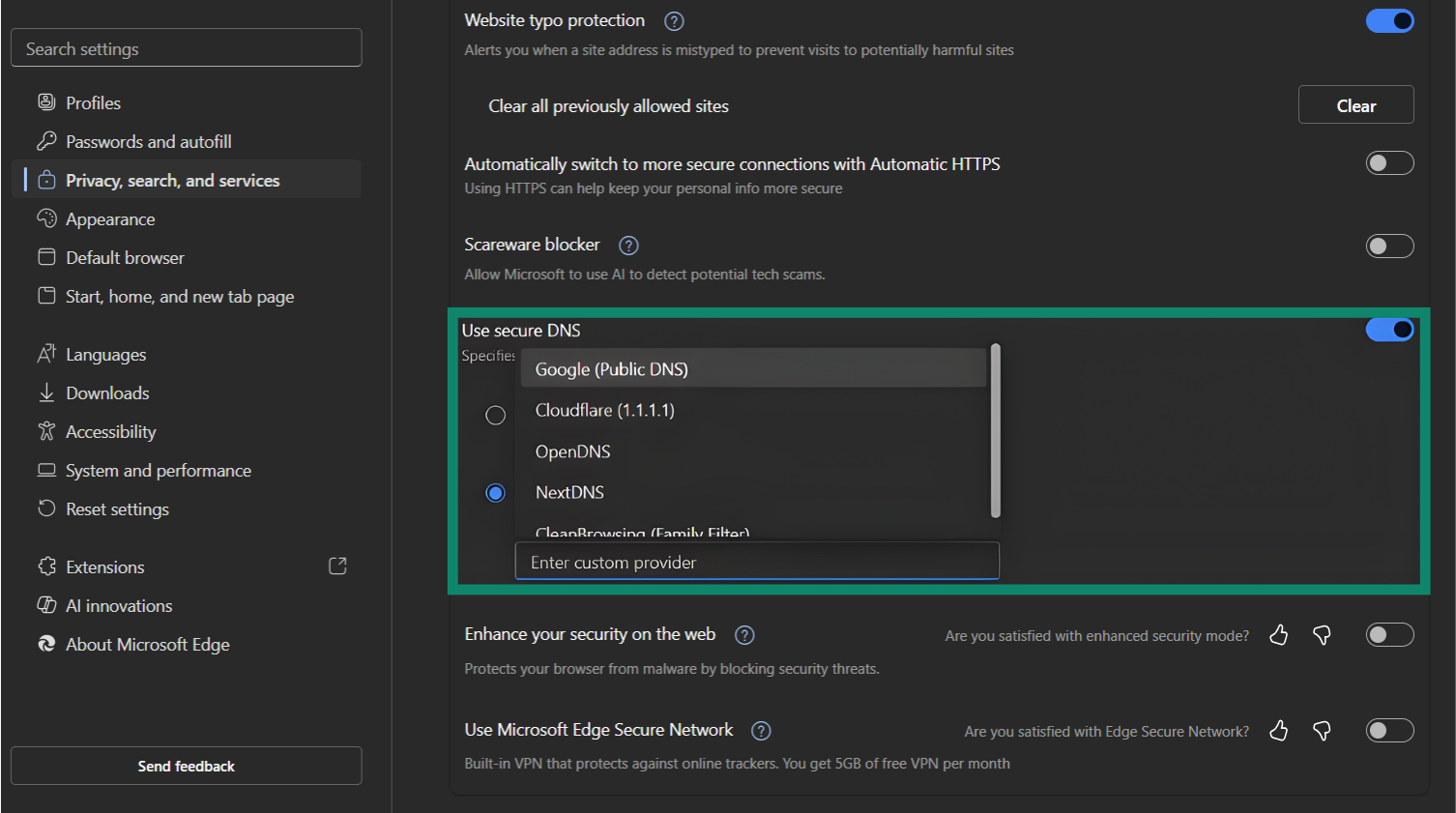
Edge includes settings to encrypt DNS lookups and block cross-site trackers. Turning these on reduces how much information is shared through your IP.
- Open your settings menu and select Privacy, search, and services.
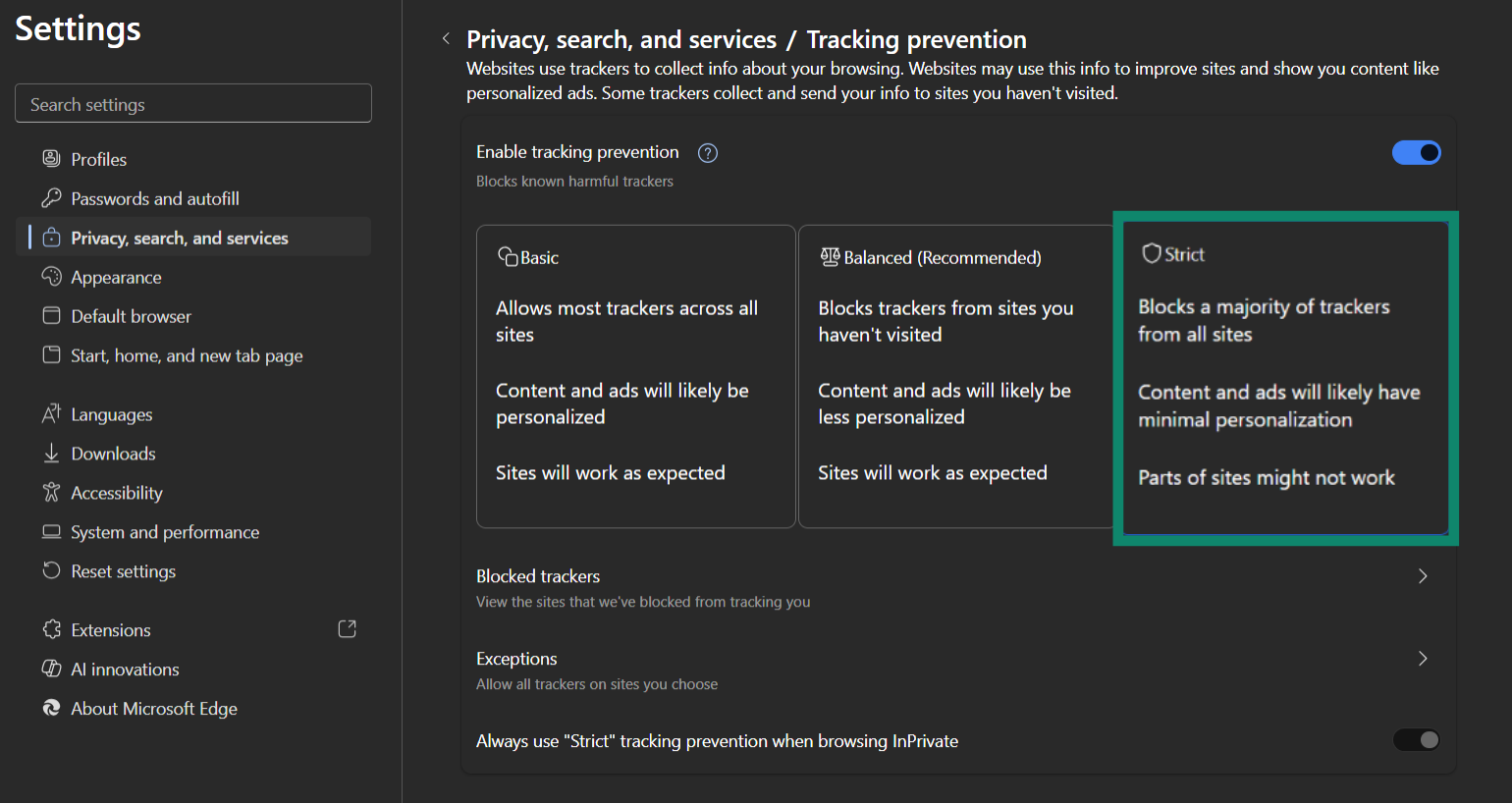
- Under Tracking prevention, choose Strict to block most third-party trackers.
- Go back to the Privacy, search, and services page.
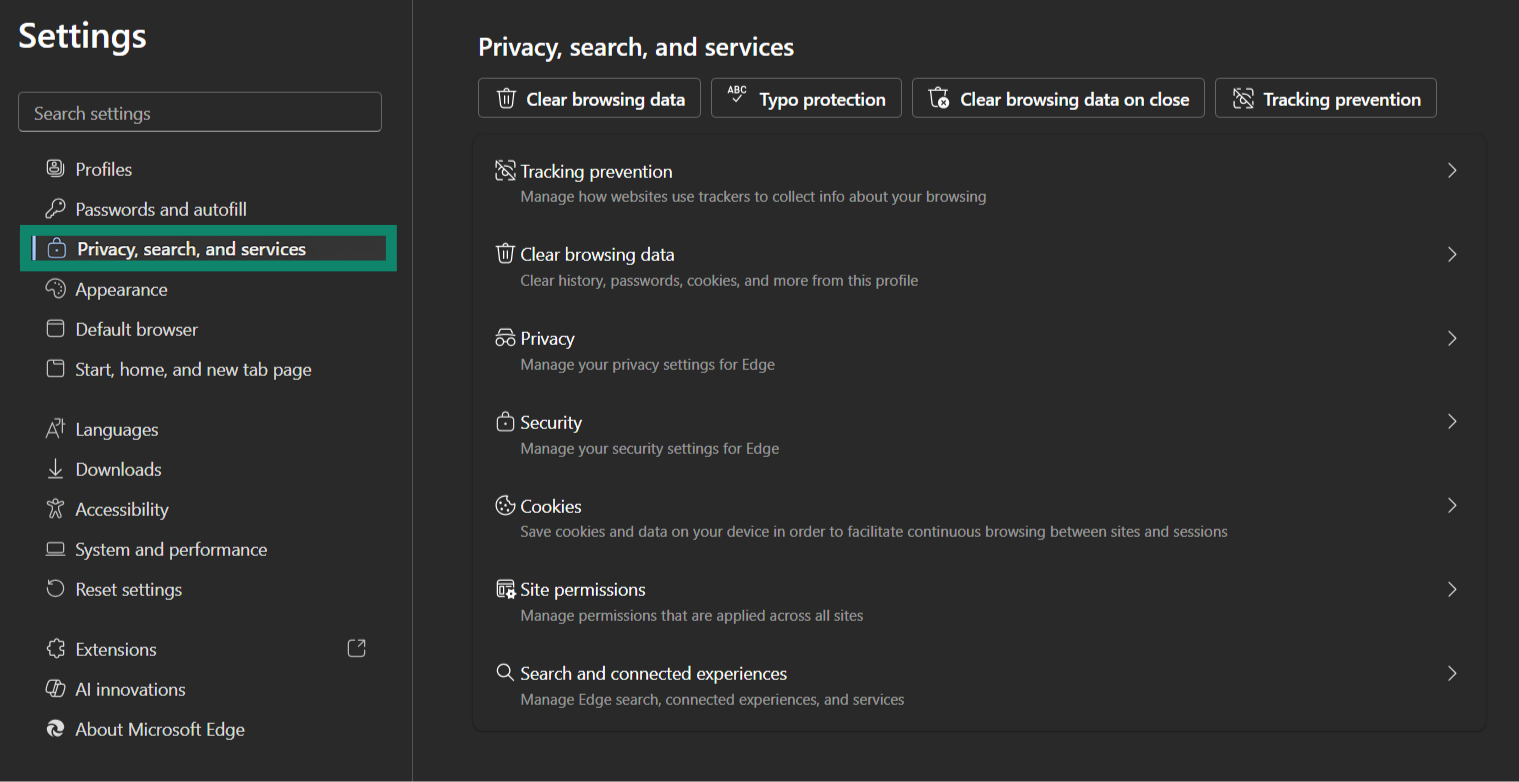
- Scroll down to Security, enable Use secure DNS, and select a trusted provider.
How to test if your IP address is still being tracked
Even when using a VPN or encrypted DNS, your IP address can still be exposed through browser leaks, misconfigured apps, or operating system settings. Regularly testing your setup helps ensure that your VPN, DNS configuration, and browser settings are protecting your privacy.
- Check IP leak websites: Use ExpressVPN's IP testing tool; if you’re connected to a VPN and the site still shows your actual IP address, then your VPN may be leaking your IP. When your VPN is working properly, only the VPN’s address should appear.
- Perform DNS leak tests: DNS leaks occur when your device queries a DNS server outside of your encrypted tunnel. ExpressVPN’s DNS leak testing tool can show you which DNS servers are being used.
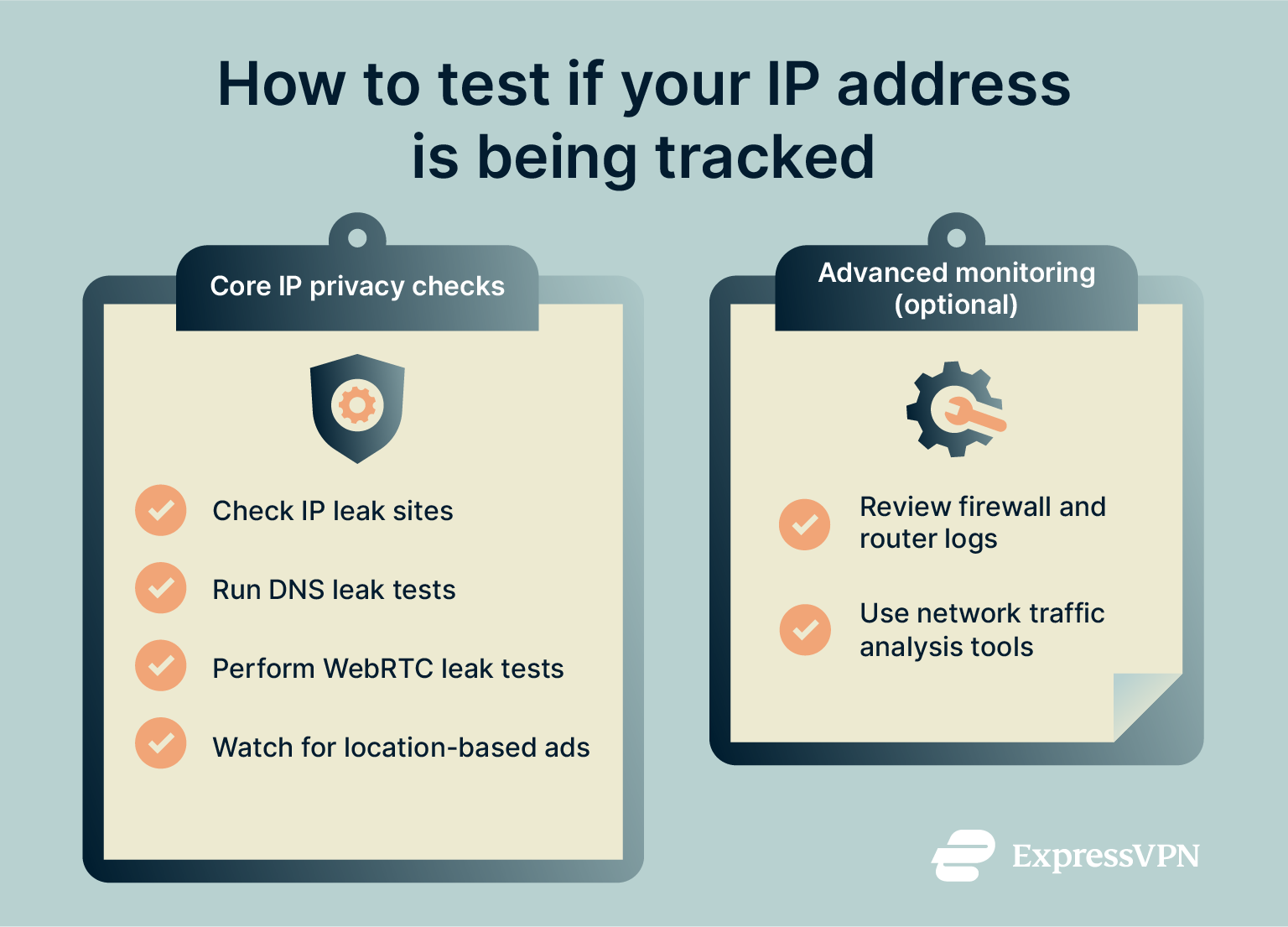
- Run a WebRTC leak test: WebRTC, a browser feature used for real‑time communications, can reveal your IP address even when you’re connected to a VPN. You can check to see if your browser is leaking using our WebRTC leak test tool. Disable WebRTC in your browser settings or install extensions that prevent WebRTC leaks, such as Microsoft’s WebRTC Leak Shield.
- Monitor targeted advertising: If you consistently see ads tailored to your location or previous browsing history, your IP address or other unique identifiers may be leaking to advertisers.
Advanced monitoring (optional)
For business owners, IT professionals, and expert users, there are a few additional steps you can take to protect yourself.
- Review firewall and router logs: Regularly review logs on your router or firewall to see incoming connections and determine if any unauthorized systems or users are connected or querying your devices. If you notice suspicious activity, such as repeated access attempts or connections from an unexpected region, your IP may already be known or targeted by cybercriminals.
- Analyze network traffic with intrusion detection system (IDS) tools: Tools like IDS monitor your traffic for unusual patterns and alert you when unknown IP addresses attempt to communicate with your device. Advanced users and IT experts can use this to identify if someone is actively tracking or attacking a network.
FAQ: Common questions about IP address tracking
What does “Limit IP Address Tracking” do on iPhone?
“Limit IP Address Tracking” is a privacy feature on iPhone that helps hide your Internet Protocol (IP) address from known Mail and Safari trackers, making it harder for advertisers and other third parties to link your activity across different sites or emails.
Is it safe to limit IP tracking?
Yes. Limiting (Internet Protocol) IP tracking strengthens your privacy and reduces your exposure to targeted advertising and cyberattacks. However, there are some drawbacks worth mentioning. Some programs and verification systems, like CAPTCHA, will flag frequently rotated IPs as suspicious and may require more verification attempts or temporarily block you.
Do browsers provide options to limit tracking?
Modern browsers are starting to implement features that mask IP addresses and limit tracking. For example, some browsers are experimenting with a two‑hop proxy architecture. In addition to proxy systems, many browsers offer built‑in blocking of third‑party cookies, tracker‑blocking extensions, and options to disable Web Real-Time Communication (WebRTC) leaks.
How often should I change my IP address?
There is no universal rule, but changing your Internet Protocol (IP) address regularly helps reduce tracking. IP rotation techniques, such as reconnecting to a VPN server or restarting your router, will assign you a new address and make it harder for websites to link your sessions together.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN